In this next installment of our Malware Terms for Non-Techies series, we’re unraveling a term you have probably come across: DLL hijacking. This method has been a key player in some recent pervasive attacks. Actually, DLL hijacking has been in use for years, causing loss of data in Windows OSs since the early 2000’s.
Dynamic Link Libraries
To really understand what’s at work in a DLL hijacking attack, we need to understand what DLL’s themselves are. DLL stands for Dynamic Link Library, which are special files that contain instructions that allow other programs to run and execute certain functions that have been coded into that one single DLL file, even at the same time. Because the code is only loaded when needed, memory is conserved as the RAM has fewer things to load, which makes computers run faster. DLL files also allow developers to share and upgrade functionalities without relinking applications, because the data can be used in several applications at once.
Understanding DLL Hijacking
DLL files are essential building blocks of the Windows OS but due to the way the search path is implemented, attackers can manipulate the system used to find executed files. This is because the OS looks for the needed DLL in a specific order by executable. If the path hasn’t been hard coded, any authenticated user can add a file into a directory by default setting.
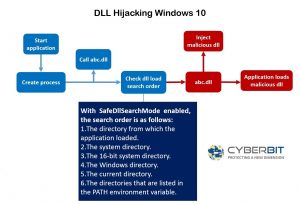
The search path:
This means that all an attacker needs to do is insert a malicious DLL file into a path that will eventually be called upon at one time or another. By figuring out the path that the DLL uses when it’s requested, an attacker can place a malicious DLL file with the same name as a legitimate file somewhere towards the top of the path so it’s reached before the real, non-malicious file is reached.
To get understand how this works, think about what happens when you want to print a document; You hit “print” which activates the .exe file, causing the DLL file to load from its location and thereby print the document. In the case where it has been hijacked, a hacker has inserted a malicious DLL in the path of the document and now it loads the malicious code.
This is an example of the path on Windows 10 operating system we can see where the malicious DLL has been inserted, thus hijacking the path:
Microsoft has made significant efforts to mitigate the vulnerability by changing the DLL search order over the years. But attackers have been able to take advantage of this new order as well with additional vulnerable programs detected in recent years.
Attacks that use DLL hijacking are fairly common, because the vulnerability persists on Windows OS and because it’s scarily easy to pull off. In August, the browser hijacker malware Youndoo was found to be resetting homepages and search engines to its own rogue, though not necessarily malicious, homepage, via DLL hijacking. Delivered inside a legitimate software freeware installation, the file planted itself somewhere in the same folder as the Chrome and Firefox browser executables. When an executable was called upon to load, the malicious DLL files loaded first, causing the homepage and search engine to switch to the Youndoo one, in place of the user’s normal Chrome or Firefox homepage.
And just last week, a new wave of the Vawtrak banking trojan was discovered, using DLL hijacking to insert itself into the loading path for MS Word documents. The malware spreads via a spam email that poses as a parking ticket notification. Once the link in the email is clicked, it asks the potential victim to enable the macros. If it enables the macros, it calls upon the malicious DLL and installs the malware to log keystrokes, take screenshots and even open backdoors that give admin access to all files, certificates and passwords stored on the computer.
Detecting and Preventing DLL Attacks
To detect DLL attacks, software developers should monitor changes to DLL files such as rename, modify or replace. Additionally, DLLs that are loaded to known software with remote or abnormal path should be tracked.
There are a few commercially available tools to detect rogue DLLs, but not all have the ability to reverse the process and restore previous state of the OS. That part might be required customization per malware. Your focus should be on hardening the OS while applying endpoint protection tools that identify malicious activity. A solid endpoint protection tool that focuses on catching anomalies to detect exactly which DLLs have been changed on the endpoint. Once identified, those files can be restored to their previous, safe versions.

