The WannaCry/WannaCrypt0r Ransomware attack has been receiving massive publicity following its severe global impact. Much has been written about WannaCry’s ability to spread rapidly by exploiting a Windows Server Message Block (SMBv1) vulnerability, AKA EternalBlue.
Upon the outbreak of the attack Cyberbit’s malware researchers took the liberty of running the ransomware on a computer protected by Cyberbit EDR – Endpoint Detection and Response. Cyberbit EDR protects sensitive organizations including financial institutions, governments, and militaries from ransomware and unknown threats that often bypass antivirus systems, by using behavioral analysis and machine learning. It also provides automated hunting and analysis aids that dramatically accelerate the analyst’s work, we used these features to understand and how WannaCry works, and visualize the attack.
Behavioral Analysis
Once we ran the ransomware, Cyberbit EDR detected the attack immediately and raised an alert. We allowed the ransomware to keep running and within seconds the EDR generated a behavioral graph on the analyst dashboard. The graph describes WannaCry’s attack pattern in detail, a process that normally would have taken hours of analyst work.
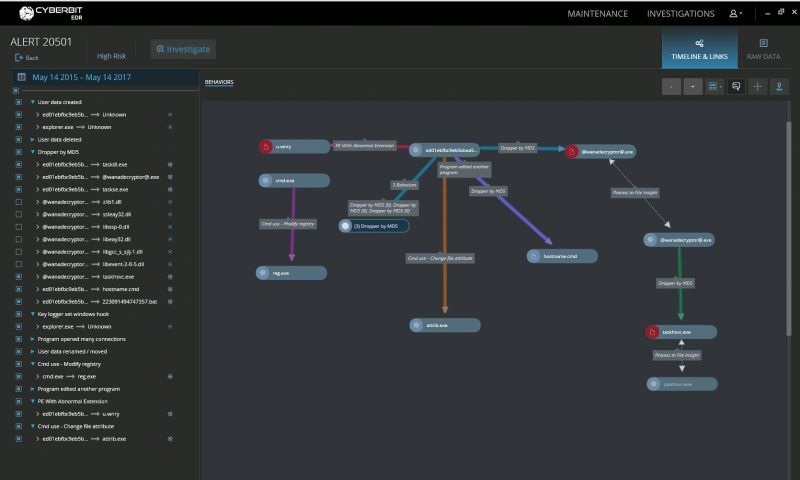
WannaCry with detailed event flow
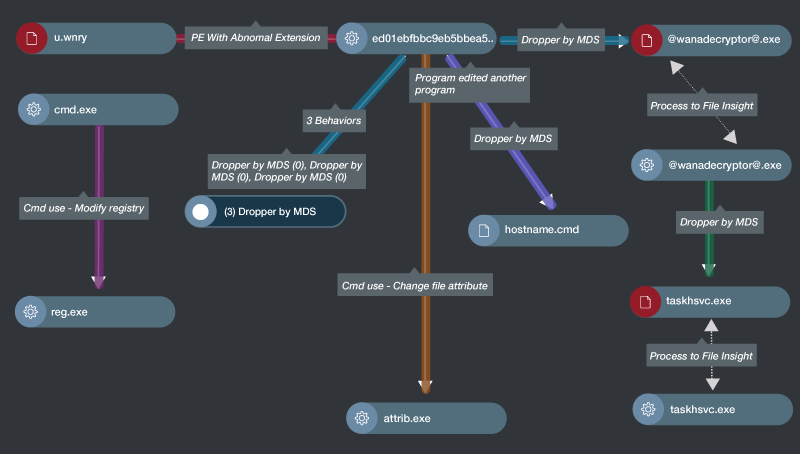
WannaCry behavioral graph – zoomed in
This behavioral graphic storyline tells us the following:
- The ransomware payload is executed and drops several files to gain persistence, as indicated by “Dropper” nodes in the graph.
- The malware initiates lateral movement by dropping hostname.cmd as indicated in the middle branch of the graph.
- The ransomware runs a command via the CMD process, which modifies the registry.
- The attributes of the dropped file are marked as hidden by using the attrib command.
Red icons on the graph indicate static file properties identified as suspicious.
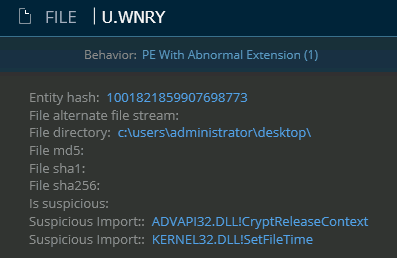
When clicking on the U.WNCRY icon, the EDR provides a drill-down view displaying the results of a static analysis of the file, which confirm that it contains suspicious import functions used in the PE import table, to encrypt data (CryptReleaseContext) and modify file time (SetFileTime):
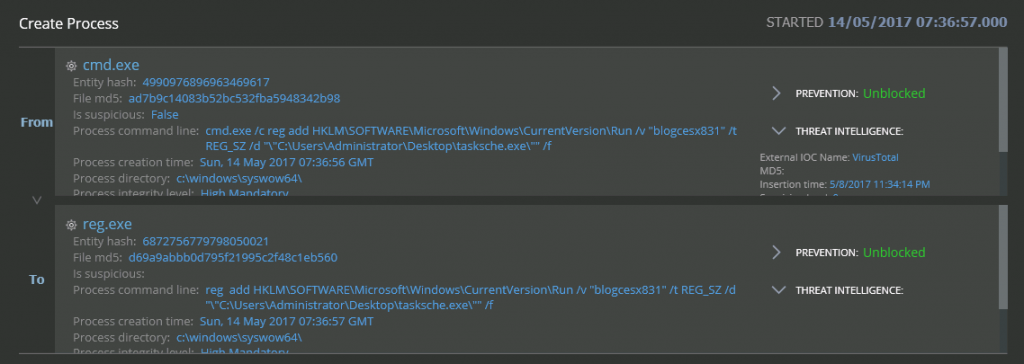
We drilled down into the CMD icon to see what exactly was happening, this revealed that a CMD batch command was used to add the malware to the registry and to the autorun list, which is a straightforward persistence mechanism:
We are happy to inform that all Cyberbit EDR customers are safe.
We recommend all customers to install the latest SMBv1 patch and to follow the best practices detailed in our previous post immediately.
If you’d like to learn more about Cyberbit EDR’s anti-ransomware features and automated analysis contact us on https://www/cyberbit.com, or contact sales@cyberbit.com.
Tal
Tal Morgenstern is Head of R&D, Endpoint Detection and Response Team at Cyberbit.

