Today industrial control systems (ICS) are used to run all types of industrial plants from manufacturing to transportation to utilities like water and energy. Most modern ICS are hybrid IT and operational technology (OT) networks, but while most IT networks are well protected by a suite of advanced security tools, the OT networks are left bare with a scrawny minimum of protection. Considering that critical infrastructure plants are set to become prime targets for highly motivated nation-state actors, it’s time to take a serious look at the state of OT security and take calculated, strategic action to harden security quickly.
Many experts in cyber security for critical infrastructure are trying to figure out why OT defense is lagging so far behind. From my experience leading cyber defense projects for military and public utility sites in Israel and governments around the world, I have noticed five contributing factors.
5 reasons ICS security investments fall behind
- Separate organizations – IT and OT are usually separate teams within the organization. They teams have different agendas and skill sets. OT personnel are oriented towards operations and keeping everything working smoothly and reliably. IT personnel have a more innate sense of cyber security and consider it an integral part of their mission. They are highly familiar with the trends, practices and tools of cyber security. The separate teams also each have their own manager and budgets.
- OT technology spans many years – Most IT managers update their software and systems at least every few years, many times much more frequently. The IT world prides itself on fast innovation and keeping pace with a constant flow of updates and new product releases. The OT world on the other hand, is responsible for maintaining and protecting computers and plant equipment which in some cases can be up to 30 years old. The boom in construction of ICS plants occurred in most of the world 30-40 years ago. Because the costs of building physical energy, water and transportation infrastructure are astronomical, they are not frequently upgraded or replaced. As new technologies are developed they are patched into the existing site, resulting in highly diverse OT networks that can include 30 year old turbines, a 3 year old PLC, a Window or Linux HMI updated last week, and everything in between.
- Heavy regulations – Most critical infrastructure plants are either owned and operated by governments or strictly regulated by them. This strong oversight creates an environment of conservativism and effects the organization and its managers. Focus is on compliance and maintaining unified standards, so innovation and change can be very difficult and slow moving.
- Excessive conservativism – OT managers are obsessive about “keeping the lights on” and rightfully so. They are burdened with a heavy responsibility. Unfortunately, this comes with an over-blown fear of change. From their point of view, if things are running smoothly and reliably now, there is no reason to meddle with anything. The fear that upgrades, changes and new equipment and software will bring with it new problems and the danger of disrupted service is too catastrophic a risk for them to bare. The result of this “If it ain’t broke, don’t fix it’ attitude is that software and hardware are rarely updated.
- The “Air gapping” myth – There is a pervasive myth that somehow OT systems are a safe harbor from cyber risks because they are not directly connected to the www like IT systems. Many IT security tools are focused on preventing outside intruders from penetrating the network via internet connections, but since ICS systems are “offline” they shouldn’t be exposed to these risks. This “air gapping” myth was punctured with the discovery of the Stuxnet malware in 2010 that jumped from the IT to OT realm and caused massive physical damage to nuclear facilities in Iran. Even if the OT network is disconnected from the internet, there are many other ways a malware can reach the ICS, especially when highly motivated and well-funded nation-state actors are involved, but nevertheless, the Air-gapping myth remains pervasive. (Read more: “Ending the air gapping myth in critical infrastructure security“
New enemy, new defense
The now all too familiar world of computer hackers was developed largely by rouge computer geeks with a chip on their shoulder or mischievous desire to see how much trouble they could cause. The original ‘script kiddies’ as they are known, were essentially the computer science version of juvenile delinquents who instead of spraying graffiti and smashing windows, used their coding skills to take down websites and break into secured networks to expose sensitive data.
Today, the potential of cyber hacking has been recognized and exploited by the most powerful international groups. Organized crime is now extorting billions of USD per year via ransomware attacks on private citizens and corporations. International terror groups and hostile nation states are employing hackers to penetrate and disrupt all types of critical networks. The list of sensitive, vulnerable targets that could potentially be hit is endless; power and water supply, airports and transportation infrastructure, hospitals and healthcare, etc.
Understanding the national infrastructure cyber attacker
It’s important to understand that the cyber attackers targeting critical national infrastructure are a special breed. They have the skills, resources, and motivation to go after the most important national targets. They are not “lone wolf” attackers, rather likely part of a large and powerful network of terrorists or hostile nation-state actors. If their motivation is money, they will be after and incredibly large sum that can be used to fund further terrorism. Most likely, they are seeking to do massive national harm, create “shock and awe” amongst leaders and the general citizenry.
Low frequency, high threat
Critical infrastructure attacks are carefully planned for long periods of time and target a specific site. Therefore, they are much less frequent than the endless barrage of IT threats; less frequent, but far more dangerous. Unfortunately, the low frequency of attacks lulled many OT leaders into thinking the cyber threat on their systems is not that serious. Many carried on blissfully, with only basic cyber security tools in place, until recently.
The last few years have shaken the OT community out of its slumber. Sophisticated cyber-attacks a German steel mill, the Ukrainian power grid and a series of other “unexplained outages” have made it clear that cyber-attacks on OT networks are on the rise and are expected to get much worse soon. As awareness grows, early adopters have already begun implementing new, updated OT cyber security defenses. State-backed public infrastructure is at the forefront of this new cyber security approach, largely due to the relative ease of getting budgets approved and proving the net value of expenditures.
Holistic OT security
While updating software and hardware is always going to be a necessary part of maintaining security, it is not sufficient to keep networks safe. Comprehensive security requires taking a holistic approach that ensures reliable protection for the entire network: from HMI to the physical machinery.
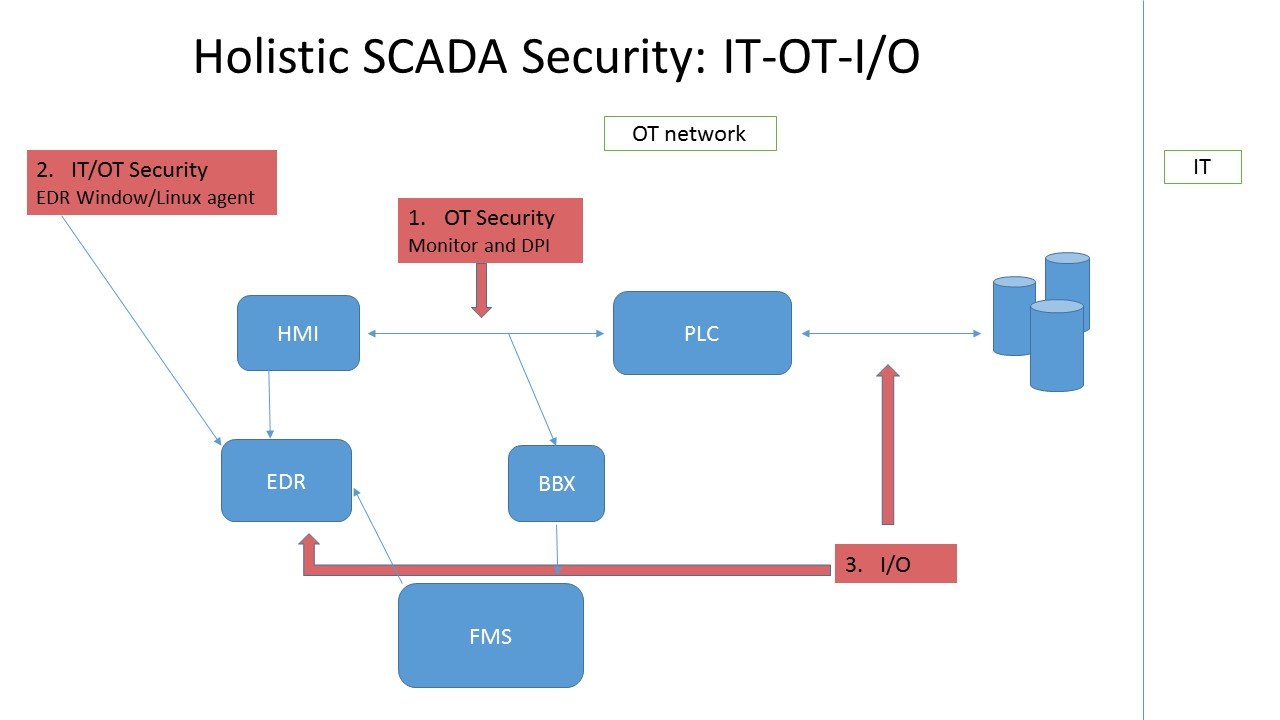
- HMI-PLC security solutions– the most common cyber security solutions in the OT world perform deep packet inspection (DPI) on the traffic between the HMI (human machine interface) where a human operator monitors and sends commands to the PLC (programmable logic controller). Most vendors provide solutions that work in passive mode monitoring this traffic, performing DPI and applying pre-set whitelist/blacklist rules. This is a very partial solution because it addresses just one important segment of the network, but leaves other vulnerabilities wide open. For example, if someone attacks the HMI or the PLC and the I/O’s, the vendor solution will not be able to detect.
- IT/OT security solutions – These solutions provide a better level of protection because, in addition to monitoring traffic between the HMI and PLC, they also protect the HMI from external attack. The HMIs are standard Windows or Linux agents that can be protected with advanced EDR (endpoint detection and response) tools. Adding this layer provides much better protection of both the IT endpoint and the commands being sent to the OT network via the PLC.
- Holistic IT/OT/IO security solutions – This solution provides protection across all 3 of the vulnerable points of attack from HMI to the PLC/controllers to the electric commands sent to the physical equipment. The final IO piece is critical because this is where the serious damage can be done. We saw in the infamous Stuxnet malware that it is possible to directly infect the PLC with malicious code that sends faulty or dangerous electrical commands directly to equipment. In the case of Stuxnet, the commands caused the centrifuges at Iranian nuclear power plants to spin at very high speeds and then suddenly slow down, causing physical damage to the aluminum tubes. It simultaneously sent normal data back to the HMI so that no abnormal behavior would be detected. This attack technique has passed the “proof of concept” stage and nation-state hackers are certainly developing new ways to gain access to PLCs and wreak all sorts of havoc by sending malicious IO commands directly to physical equipment in utilities, healthcare, transportation and more. Therefore, the final segment of a holistic cyber security solution for SCADA must include IO protection.
Manage cyber events from a single dashboard
Holistic IT/OT/IO SCADA security solutions must also provide a single, unified dashboard to control and manage cyber events from one console. This unified view is critical since SCADA networks are so large and diverse. It is impossible to tighten security and react effectively without a user interface that gives the OT security manager clear visibility of the entire network architecture, activity, and alerts. The same unified dashboard enables fast detection, investigation, and response to any cyber event.
Though the holistic IT/OT/IO solution is clearly superior, in the eyes of many OT operators it sounds more like science fiction than a practical solution. Only the most innovative OT managers, with the necessary budgetary support and executive mandate, have successfully implemented holistic security solutions that provide end-to-end protection. This is the right direction and the market will continue moving towards it.
Protect the entire IT/OT/IO attack surface
If we start by understanding attackers and their motivation, infrastructure hackers are highly strategic, sophisticated and well-funded. It is imperative that we take the same approach to defending them. Now is the time to overcome traditional conservative approaches and pervasive “air gapping” myths to embrace and deploy an advanced, holistic security strategy that will keep critical OT infrastructure safe against developing cyber threats.
Itche Weinreb is VP Product at Cyberbit

