ESET researchers recently discovered one of the most aggressive forms of cyber threats on electric grids and industrial control networks – coined Industroyer, or CrashOverride. This malware was likely the cause of the December 2016 “Black Energy” cyberattack on Ukraine’s power grid that caused a blackout of over an hour in part of its capital, Kiev, and is considered the biggest ICS/SCADA threat since Stuxnet. Industroyer is only the second known malware after Stuxnet designed specifically to attack industrial control networks. It can take control of electric substation switches and circuit breakers and can turn off power distribution and seriously damage equipment.
The Growing OT Threat
OT cyberattacks rising sharply as a result of the increased modernization and connectivity of industrial facilities. Operational (OT) networks are decades old and contain a wide variety of controllers (PLCs/RTUs), making them easy targets. High profile attacks such as Stuxnet, Black Energy and the 2014 attack on a German Steel Mill, have raised global awareness to the vulnerability of industrial networks and the disastrous consequences of such attacks.
OT Attacks – the Risk Starts at the IT Network
The common factor in all known OT cyberattacks, often overlooked, is that these attacks have not started in the industrial control network, but have initiated in the IT network which is easiest to penetrate. Stuxnet, for example, is believed to have been introduced by means of a USB stick, after which it moved into the sensitive OT network to attack nuclear centrifuges. Operational devices are controlled by IT workstations such as HMIs running on Windows machines. Surprisingly, OT managers are often unaware of the need to provide the same level of protection to the IT network.
This is an illustration of the IT to OT Threat Stack
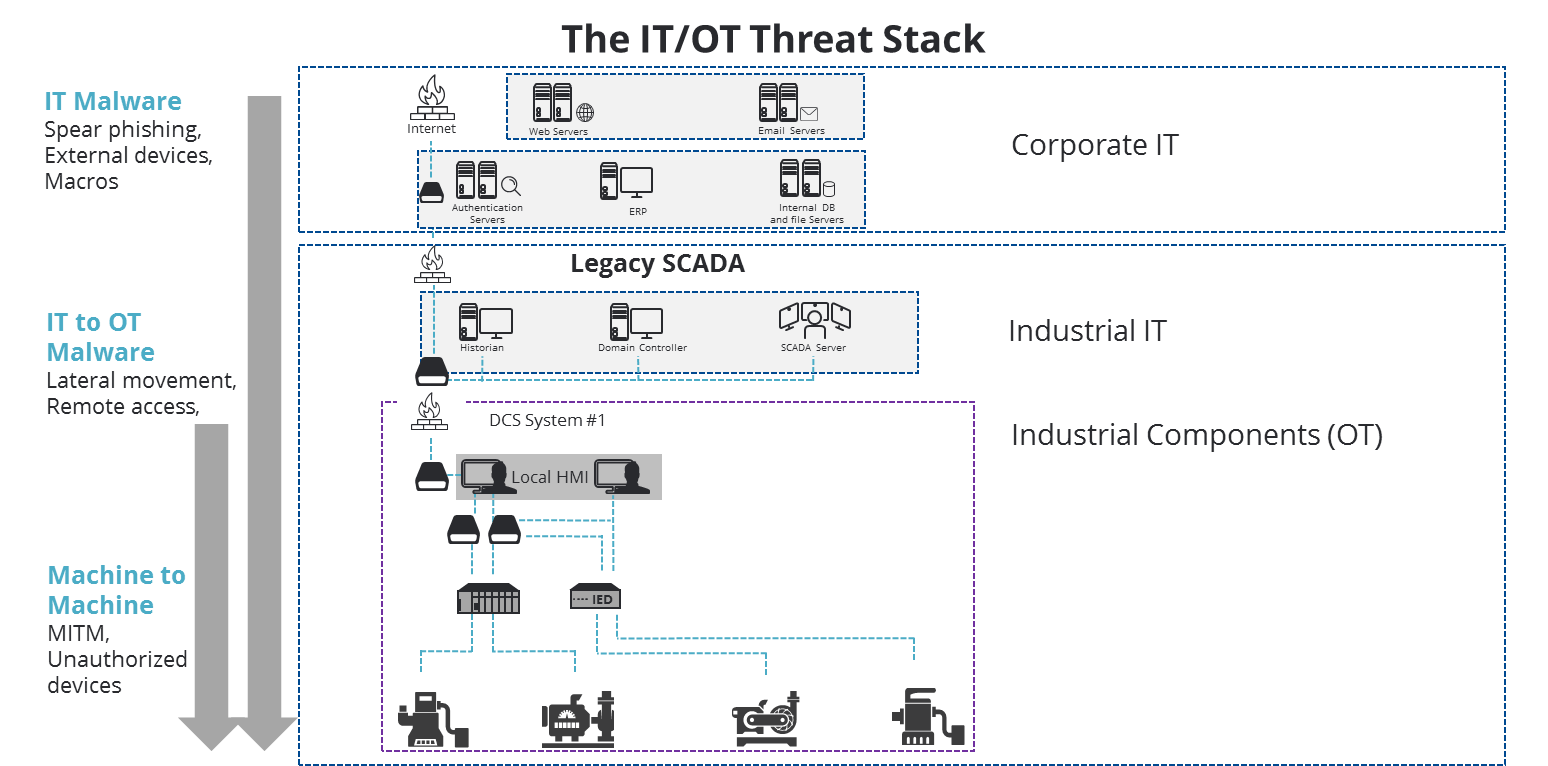
Industroyer – the IT to OT Infection Path
As analyzed by ESET – Industroyer is an IT to OT attack which begins by infecting the IT network.
Once Industroyer has penetrated the organization it begins searching for PLC/RTU controllers. Once the controllers are identified, the malware waits to launch its attack at the most opportune time, like late at night, when OT Managers are slower to respond.
Then – Industroyer goes into action and launches a denial of service (DOS) attack taking the target controller out of service and, in the case of BlackEnergy – cause a major blackout.
How Industroyer Attacks the OT Network
Industroyer/ Crash Override exploits known vulnerabilities in four protocols common in power networks and sends custom crafted packets that overload the specified PLC/RTU.
Targeted Controllers:
- IEC 60870-5-101 (aka IEC101) (Serial-communications based protocol)
- IEC 60870-5-104 (aka IEC104)
- IEC 61850 – Goose
- OLE for Process Control Data Access (OPC DA)
How Industroyer Evades Detection
Industroyer uses a unique and sophisticated way to evade detection, by injecting its payload into the notepad.exe application. It is executed by running Notepad.exe using a unique runtime parameter which then skips the standard Windows code and executes the malicious code hiding in the notepad executable. This approach enables the malware to hide within a trusted application, and to be executed as a trusted application, thereby evading detection by traditional antivirus systems.
Why Do Conventional Security Solutions Fail to Detect Industroyer?
Industroyer starts with a sophisticated attack on the IT network, employing advanced evasion tactics, and moving to the OT network to attack the electric grid. This multi-vectored attack requires advanced security measures both on the IT and OT networks, and centralized management, which enables security managers visibility across the entire network. However, according to Gartner, over 60% of industrial organizations have not started, or are at early stages of constructing an IT/OT security organization and management process, which is essential to detect and respond to multi-vector attacks.
4 Ways Cyberbit Protects Against Industroyer/ Crash Override
As the first full-stack, IT/OT security provider, Cyberbit’s vision aligns IT and OT security from its foundation. By offering Endpoint Detection and Response, ICS/SCADA Security, and an overarching SOC Automation and Orchestration Platform tying both platforms together, it enables industrial organizations to addresses the entire detection and response cycle for multi-vector attacks.
Here are key ways Cyberbit helps organizations protect against Industroyer
- Endpoint Detection and Response to Reduce the Impact of Evasive Tactics – Industroyer is dormant on an endpoint in the IT network while it searches for PLCs to attack. During this time, it uses evasion techniques to remain undetected by conventional signature-based security systems, and therefore requires a next-generation, signature-less detection mechanism. Cyberbit provides endpoint detection based on machine learning and behavioral analysis immune to evasive tactics such as those used by Industoyer.
- IT/OT Security – Detect Before the OT Network is Affected – Industroyer, and similar IT/OT attacks may spend hours or weeks in the IT network researching the network prior to identifying an OT device to attack. Deploying an advanced detection system in the IT network means that attacks can be identified BEFORE reaching the sensitive OT network. The conventional approach of focusing on OT security means that an attack may be detected weeks after it started, and when risk is just minutes away.
- Deep Packet Inspection to Discover OT and Detect communication – in the event that an attack was able to reach the OT network Cyberbit employs ICS/SCADA Deep Pakcet Inspection (DPI) to detect malicious communication across a wide range of ICS/SCADA protocols including serial protocol monitoring – IEC101 in the case of Industroyer.
- Multi-Layered SOC Management – the OT Security reality requires visibility and incident response management across both IT and OT networks. Cyberbit provides SOC Automation, Orchestration and Analytics which orchestrates IT, OT and IoT security alerts to manange the response starting with the alert, to automating the incident response and investigating the date collected across the entire IT and OT Network.
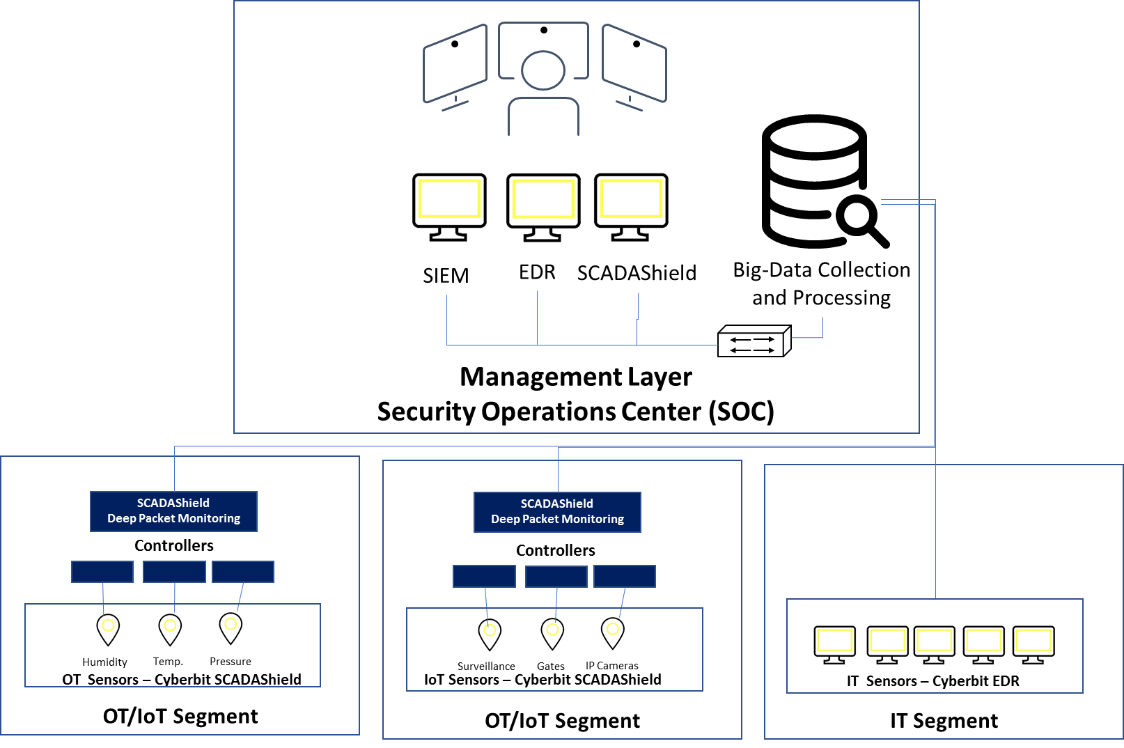
Cyberbit Sample IT/OT/IOT Deployment Scheme – Smart Building
Cyberbit SCADAShield achieves a perfect 100% score in the first ENCS comprehensive assessment of OT IDS solutions.
Download Aligning with Tier 4 NIST Framework for Critical Infrastructure Cybersecurity
Daniel Cohen-Sason is SOC 3D and SCADA Development Manager at Cyberbit

