Industrial Control Networks: a Hybrid of OT and IT
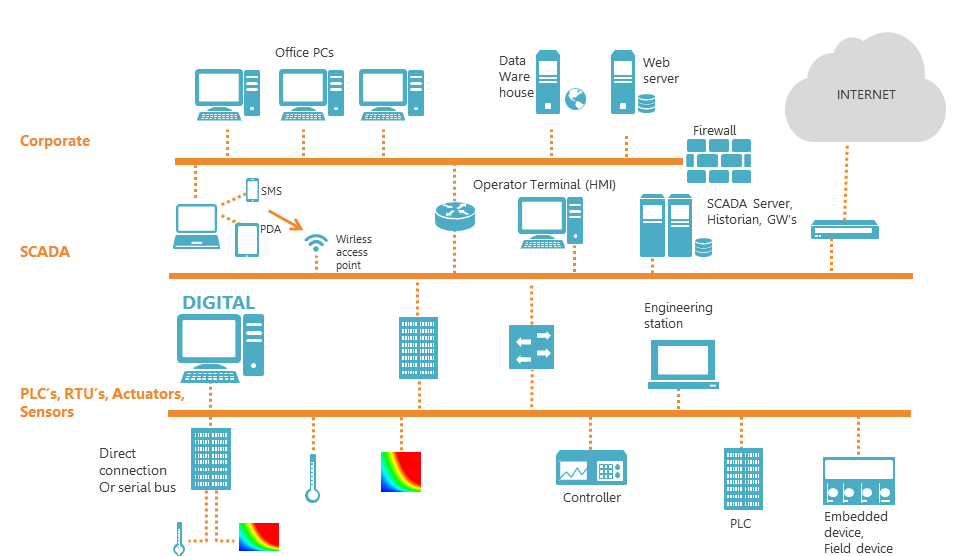
When we think about protecting critical infrastructure operational technology (OT) networks, the common perception is that it’s all about SCADA security. But that is not even half of the story. Almost all Industrial Control Systems (ICS), in critical national infrastructures as well as in much smaller localized controller-run systems, are a hybrid of IT and SCADA networks. As can be seen in the below diagram, the SCADA networks manage the operational systems themselves, but in 99% of the cases they are operated by, and report to a Human Machine Interface (HMI) Application layer, typically running on a Windows operating systems and residing in the IT network. Moreover, in most instances, and especially in large scale operations, these layers are directly connected and sometimes even controlled by the corporate IT infrastructure – interfacing and reporting to the same operation centers, the same ERP, security tools, etc. Here is what this hybrid network setup typically looks like:
Hybrid IT/OT Network
Stuxnet – the Classic IT to OT Attack
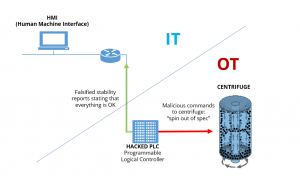
Now it is clear why most of the known and unknown cyberattacks are multi-vectored. In most cases, penetrating through the more accessible IT network and moving towards critical OT infrastructure. I expect this trend to continue and grow exponentially as IoT technology becomes a key component of enterprise network infrastructure. This is clearly demonstrated in the well-known Stuxnet attack. Stuxnet was the first known example of a weaponized malware; a targeted attack against the nuclear plant in Natanz, Iran. Despite being a fully air gapped plant, hackers managed to compromise it on multiple occasions by first infecting several companies that contracted with the plant to provide industrial control and processing products and services. The malware propagated itself via USB drives until it infiltrated the plant. It then reached vulnerable Siemens Programmable Logical Controllers (PLCs) that controlled centrifuges used to enrich uranium, as well as gas pipelines feeding into them.
Once it reached the PLCs, the malware was used to send faulty commands to the centrifuges instructing them to spin out of spec. This caused physical damage to the aluminum cylinders and took them offline. Stuxnet was a stunning cyber warfare operation that proved the ‘air gap’ is easily breached and exposed the vulnerability of IT/OT connectivity.
Stuxnet Attack Workflow
Unfortunately, although IT to OT attacks are the most common way to infiltrate critical infrastructure networks, and pose substantial risk, cyber security concepts and tools have not yet stepped up to provide an answer to these multi-vector attacks, and they remain an unsolved enterprise OT security black hole.
Vendors Solve What They Know, Instead of What Needs to Be Solved
The reason behind this anomaly, is that no companies have mastered both IT and OT technologies. Most of the information security vendors address the IT world, but have not mastered the specifics of the nascent OT market. ICS/SCADA security vendors, which today are mainly small startups, do not have the know-how, the deep pockets or the technologies to address a complicated, multi-disciplinary security problem and they prefer to focus on monitoring SCADA networks using the popular, but barely effective DPI (deep packet inspection) approach, which monitor low-level SCADA communication.
How to Mitigate Multi-Vector Campaigns Effectively – Lessons Learned from Stuxnet
Organizations are missing an effective solution to multi-vector campaigns. In order to achieve this, they must first take control and monitor all hardware devices in their hybrid network – both the SCADA drivers and the Windows/Linux endpoints. They must seamlessly supervise them, and collect bits of information into a unified big-data repository that will enable them to detect these advanced malware including their lateral movement from IT to SCADA networks and vice versa.
Secondly, organizations must acknowledge that the popular DPI monitoring for SCADA networks is simply not enough. Would you rely solely on inspecting network protocols to protect on your IT networks? Obviously not. So why would you rely on them exclusively to protect your critical SCADA network?
The only way to solve this complex challenge is by providing a layered, multi-technology solution. Multiple agents monitoring endpoints and controllers, DPI to monitor the network, big-data analytics that processes the entire spectrum of this aggregated information and produces insights that cannot be seen by siloed systems, and finally – offline and online forensic tools.
To detect and respond to the newest, most advanced malware – this is the only way to go.
Adi Dar is the CEO of Cyberbit

