Critical infrastructures such as power, oil and gas, water treatment systems and transportation are vital to national survival. Any interruption can put lives at risk. Though ample precautions are taken to secure physical facilities and separate operational networks from IT networks, the majority of ICS/SCADA networks remain vulnerable. Improving SCADA security is a top priority for every OT manager and the first and most critical step is gaining visibility.
The SCADA Visibility Problem
With some ICS/SCADA networks dating back to the 1960’s, these networks were built with reliability and manageability in mind. Many of the devices used in SCADA networks still use legacy technology such as RS232 serial (2- way communication) ports, and non-IP protocols for network connectivity.
Then things started getting messy;
Over time, legacy SCADA devices, originally offline, began connecting to corporate networks and to each other.
To ensure that supply and production run smoothly and for controlling and monitoring purposes, operators take these devices and connect elements to take the serial connections and encapsulate them over the TCP/IP protocol. Many of these devices are uniquely identified in the SCADA protocol and with the right tools and knowledge they can be discovered and attacked by malicious actors. Moreover, plant operators and IT teams are often unaware of what assets/devices, processes, configurations, and protocols are connected and running on their networks.
SCADA Security – the Blindspots
This complexity creates dangerous blind spots where attackers can easily breach any one of these unaccounted for and therefore unprotected elements.
In this fractured environment, all an attacker needs to do is hit the HMI or the SCADA server. These simple computers, used by operators to monitor processes, typically run older and unpatched operating systems and aren’t usually protected by anti-virus tools. They also contain all the access and permissions attackers need to breach the devices behind the terminal server.
In an attack, hackers will probably start with reconnaissance: They may scan IP ranges in the network, often looking for devices that have port 502 open (MODBUS). Once they have the results, they start mapping and identifying those assets. Next, the attackers can brute-force all the discovered device IDs. In response, those devices provide vendor and version information so the attackers can continue their assault, knowing exactly how to proceed.
Understanding what’s at stake, researchers infiltrate SCADA networks to prove to critical infrastructure organizations just how vulnerable they really are; Back in 2015, a team of whitehat researchers entered a well-known oil and gas corporation’s SCADA network within a week of attempts.
A simple Google search led the researchers to the name of a third-party networking gear supplier who had recently won a contract with the company. They downloaded the user manual and gained easy access using the manufacturer default password “adminadmin” that had been left unchanged.
Visibility – You Can’t Protect What you Can’t See
The only way to eliminate these blind spots is to understand the network, its devices, protocols, configurations, events, and traffic with precision; The key to making sense out of complex SCADA networks lies in visual, automatic mapping.
Automatic network mapping reveals a complete, accurate and detailed picture of the entire SCADA network, immediately discovering all network devices, configurations, processes, events, traffic, and protocols. It identifies potentially vulnerable IT/OT touch points and highlights configuration issues and unexpected changes, all in a clear, visual map.
Automatic network mapping lets Operators and IT teams see the entire network in real-time and understand what is happening and how to address potential vulnerabilities. For example, it identifies standard protocols and unique IDs like PLCs, checks for differences, updates the SCADA automatically and can be easily exported to update firewall whitelists. Once the entire network is mapped and whitelists and blacklists updated, they can then investigate and monitor all transmissions within their network and identify what activities are being caused by actual threats and which are due to operational malfunctions.
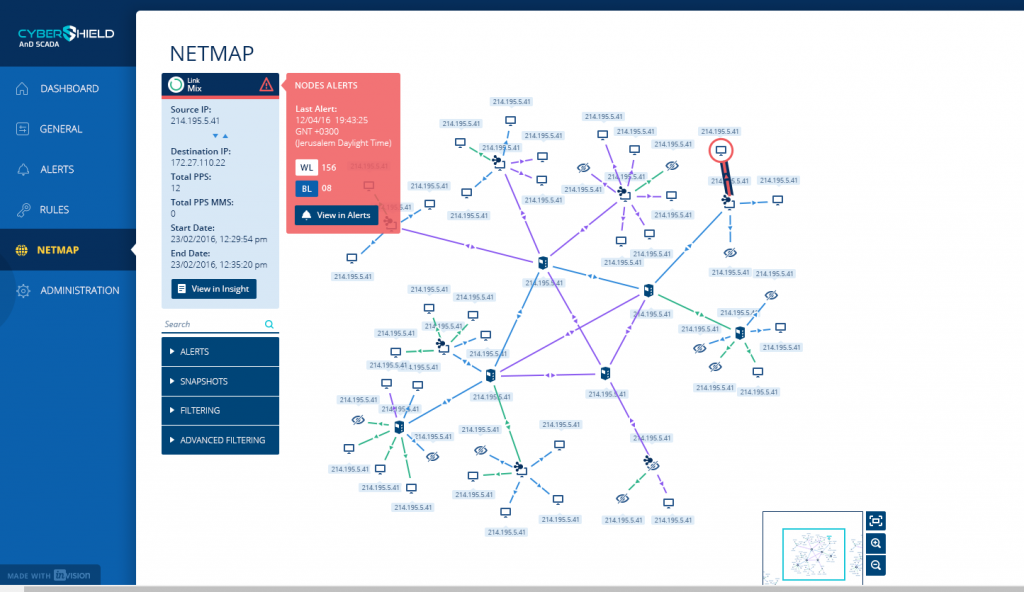
Automated Network Map, Cyberbit SCADAShield Product
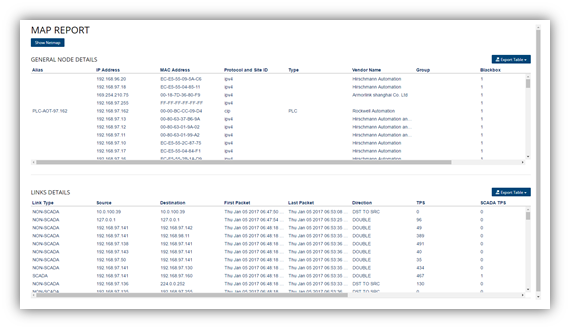
This map export provides visibility and the ability to discover new assets and report them to the network manager
SCADA Security Starts With Visibility
The hybrid nature of SCADA networks makes them difficult to accurately map and keep updated, so they remain tangled mysteries. The vast majority of critical infrastructure organizations are still suffering from network blindness and therefore wide open to attacks. Full network visibility is the first step toward better SCADA security; the simple act of creating a complete, accurate map of the network creates visibility critical to understanding and securing vulnerabilities. The first step to ensuring OT networks are safe from malicious cyber attackers is to open our eyes and take a good hard look at our networks.
Daniel Cohen-Sason is SCADAShield R&D Lead at Cyberbit

