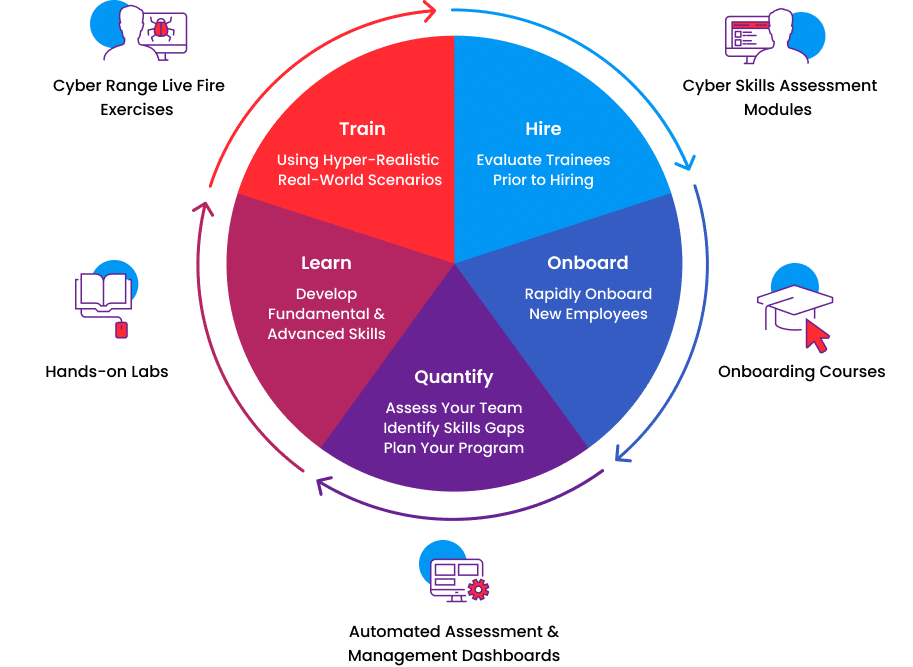
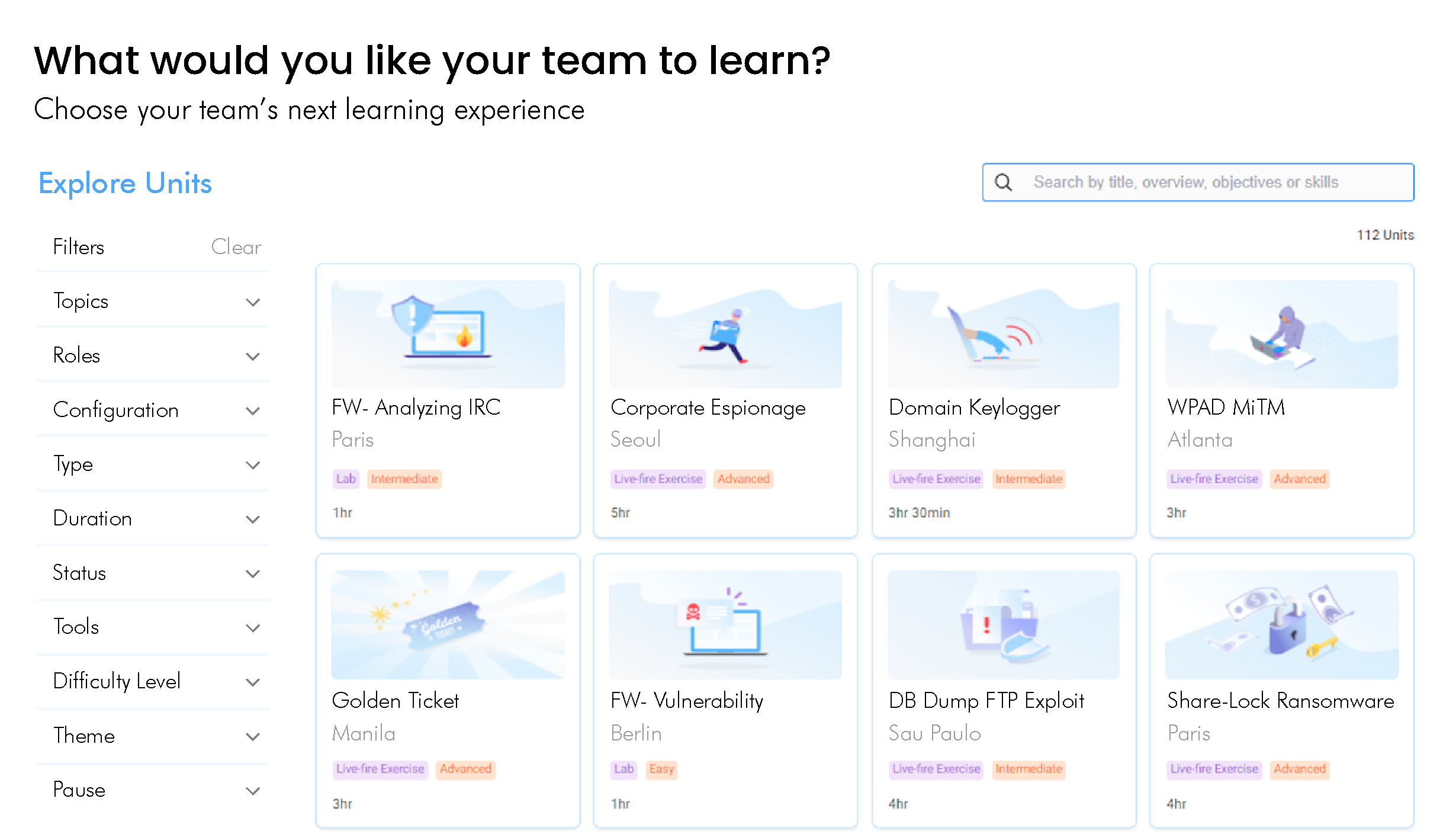
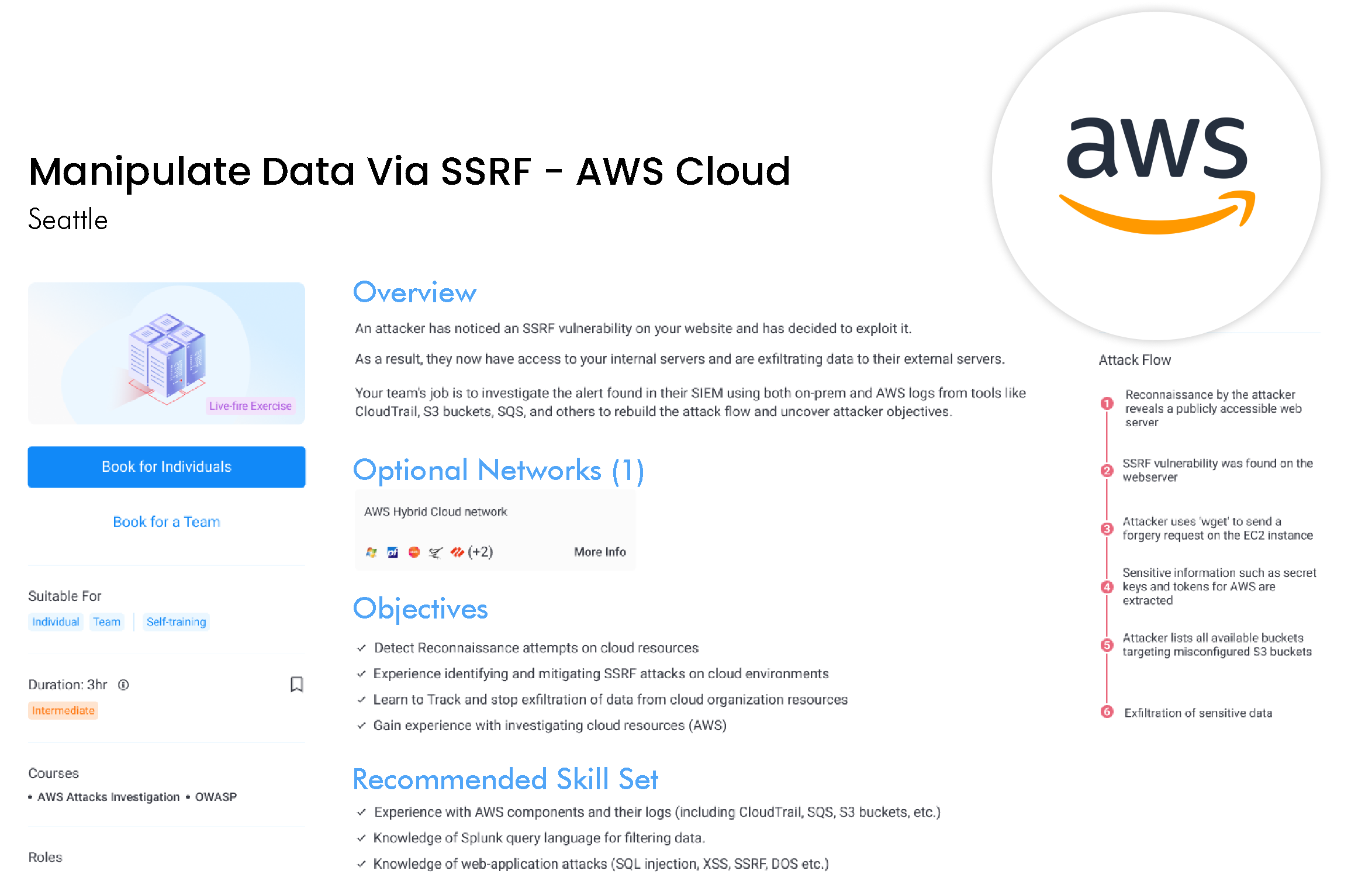
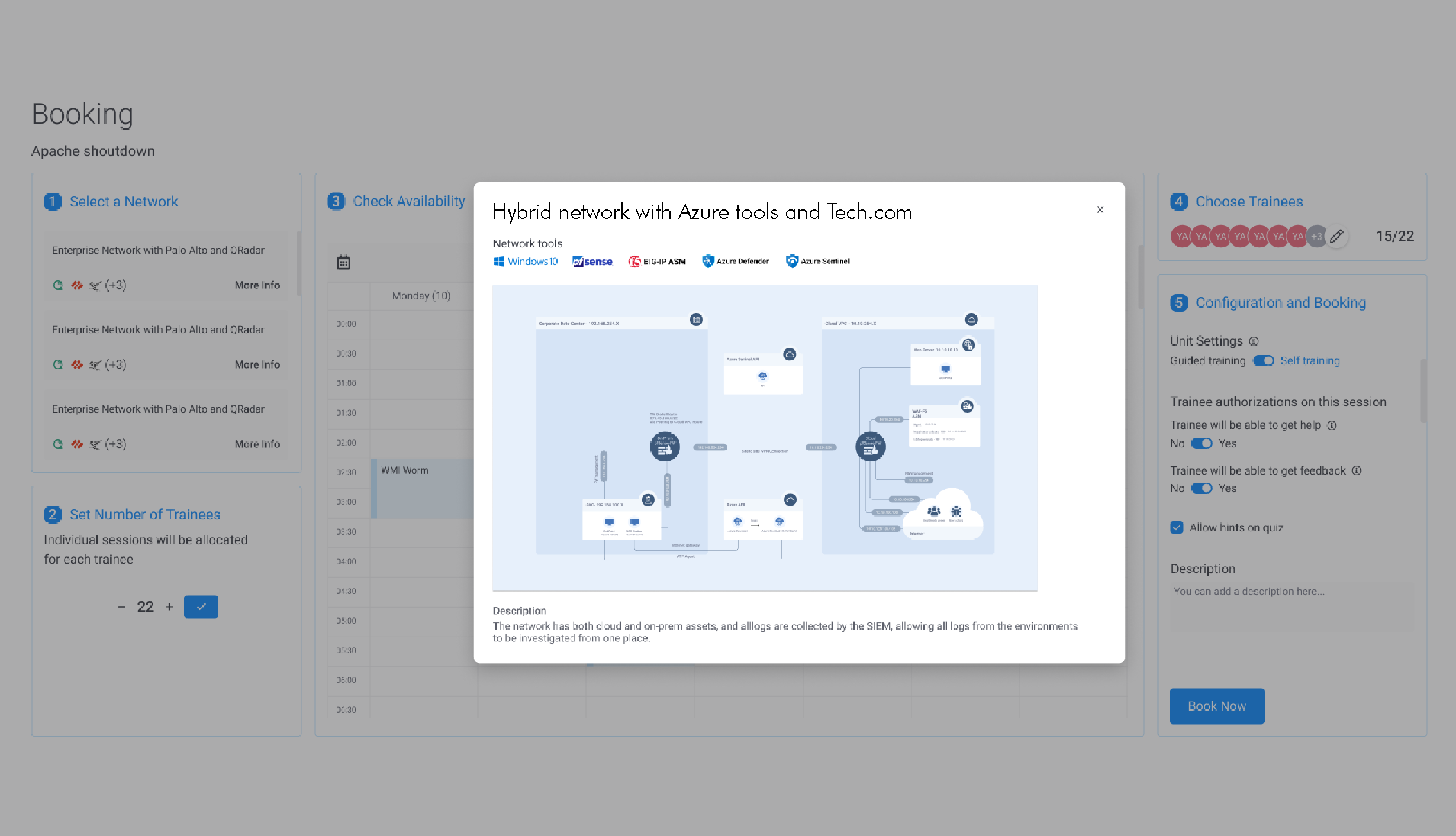
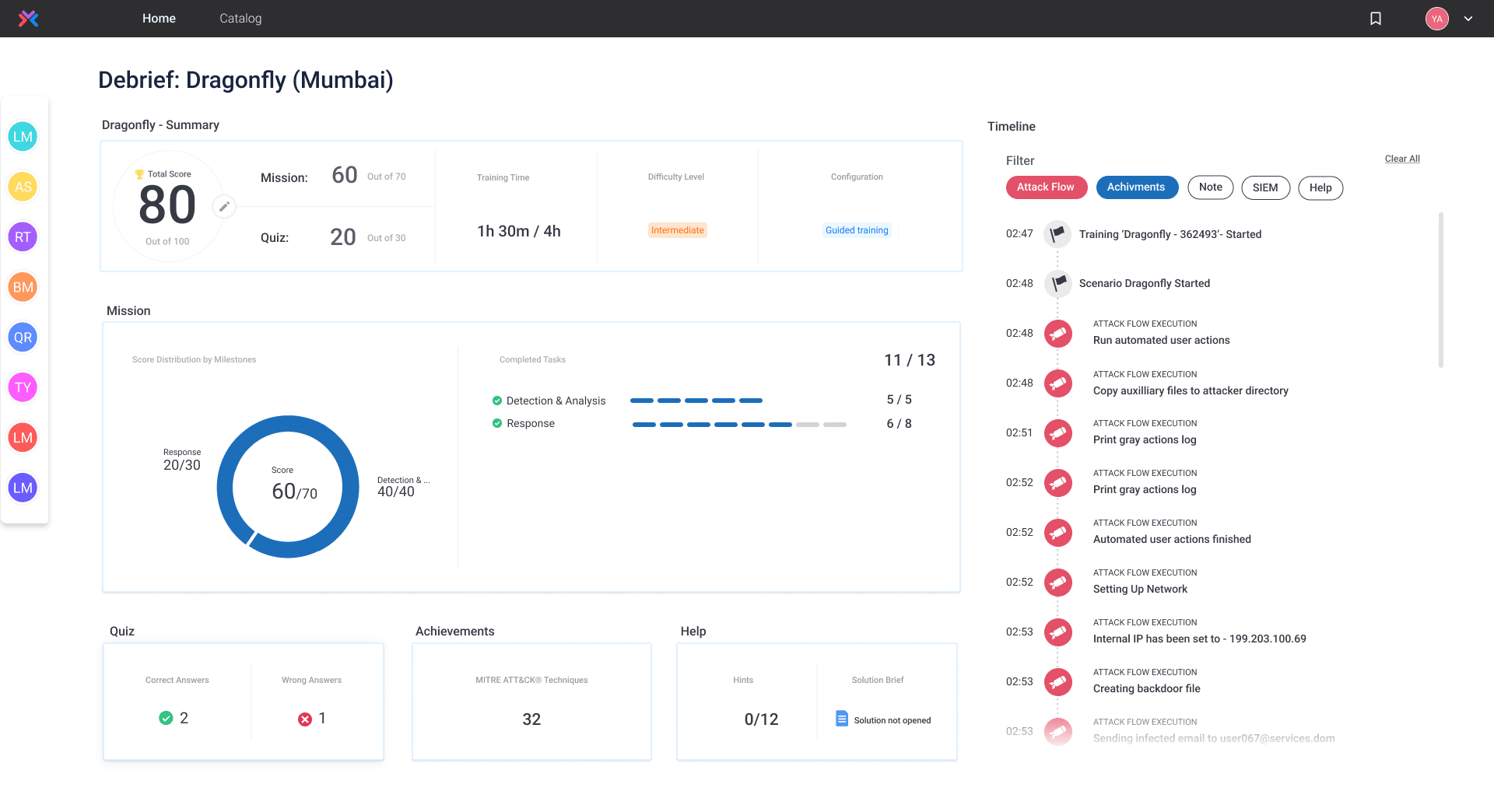
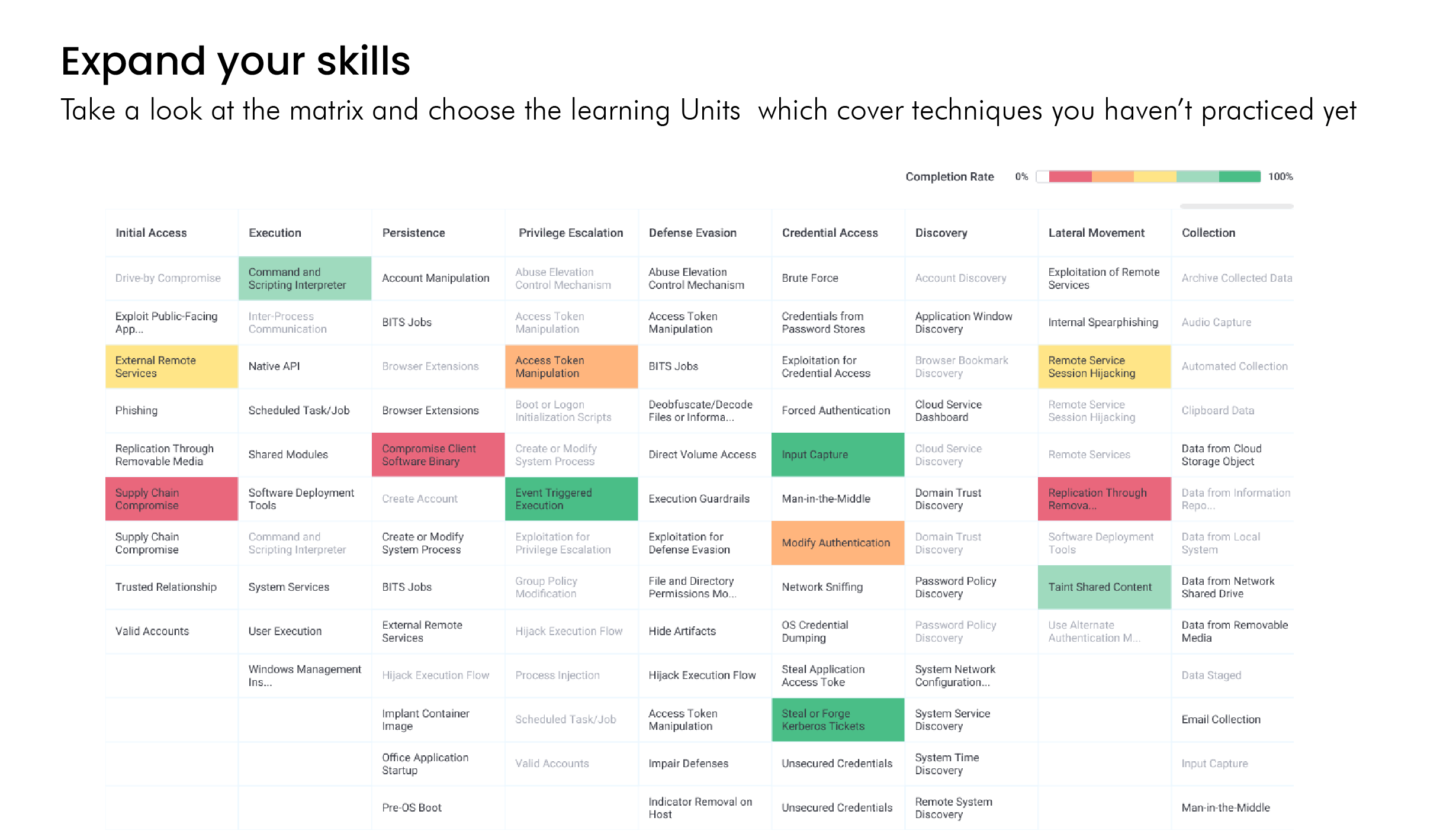
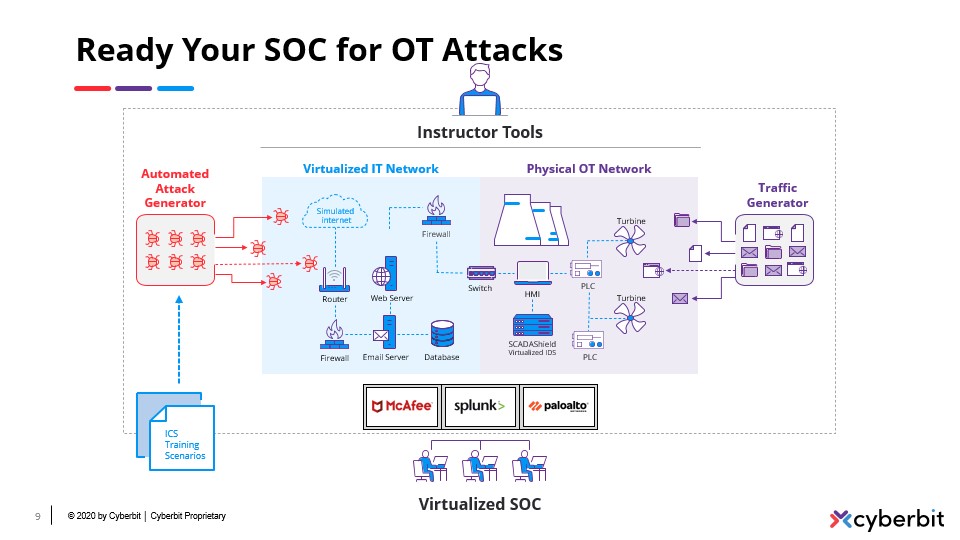
Cyberbit includes the world’s most advanced cyber range, available on-demand. Immerse your team in hyper-realistic, simulated attacks on the included cyber range to take their experience, skillset, and teamwork to the next level. Cyberbit’s live-fire cyber range simulations are the closest your team will get to a real-world incident. By training in cyber range exercises your team will excel, both technically and mentally, when the real attack takes place.