Over the last months, we’ve witnessed a significant increase in the number of cyberattacks, their severity and their ability to spread in minutes throughout the globe, infecting thousands of networks.
The central and most critical component in fighting these advanced threats is the security operations center (SOC). The increase in volume and complexity of threats is driving exponential growth in the number of enterprises that are building and running SOCs in various shapes and sizes. The EY 2016 Global Information Security Survey shows that 56% of surveyed organizations have indeed set up a SOC. This number will continue to grow, as more organizations realize the need for centralized and consolidated cybersecurity incident prevention, detection, and response.
Several years ago, organizations considered the SIEM as their central SecOps management system and built their SOC around it. This made sense at that time when the primary SecOps requirement was to centralize log collection and management and to perform basic correlation and alerting for detection. But more recently, security organizations are growing to understand that while a SIEM is an important building block within their SOC, it is no longer effective or sufficient for managing incident response.
Today, organizations are threatened by complex and persistent attacks from multiple vectors and are required to respond within minutes. On top of this, they are overwhelmed by a massive number of alerts and an ever-growing number of security tools. This required a new layer on top of the SIEM – which resulted in the birth of the SOC Automation and Orchestration platforms.
These tools attempt to streamline event management, automate playbooks and procedures, coordinate between SOC team members, effectively manage the SOC shifts and of course, integrate seamlessly the entire portfolio of security tools and feeds.
These new approaches and capabilities have matured the SOC, bringing it to new levels of functionality. SOCs can now manage more complex and longer campaigns, handle thousands of alerts and events per day, document and regulate breach management procedures and align cross organizational operations, particularly addressing the challenge of aligning security with IT operations.
And yet SOCs are far from effective. The recent Petya and WannaCry attacks are only 2 examples showing us that organizations that were hit by malware fail to manage the response in an effective way, resulting in massive spread and damage after the threat was detected.
So, what are we still missing?
When the June 3rd London Bridge terror attack that claimed 8 victims was analyzed, experts pointed at the overload of intelligence data, and the lack of resources to process it: numerous snippets of information, terabytes of chatter, tipoffs, sightings and wiretaps that cumulatively could have helped form the intelligence picture. The data was there, but the intelligence operation lacked the systems and the human resources to process, decode and contextualize it – resulting in attackers slipping under the radar.
Over the last 2 years, cyber security operations have grown to resemble military and counter-terror operations. A military operation without data and intelligence is ineffective. It is essential to invest technology and resources in collecting and processing the data to generate insights that headquarters, as well as the commander in the field, can use to make well-informed decisions in real time. The same rationale applies to cyber security. Unless we’ll be able to investigate, build a comprehensive picture of the entire threat landscape, and leverage the endless amount of information generated by the numerous sensors we have deployed in our networks and endpoints, we will fail to detect and stop malware before it is activated and causes the damage it was intended to conduct.
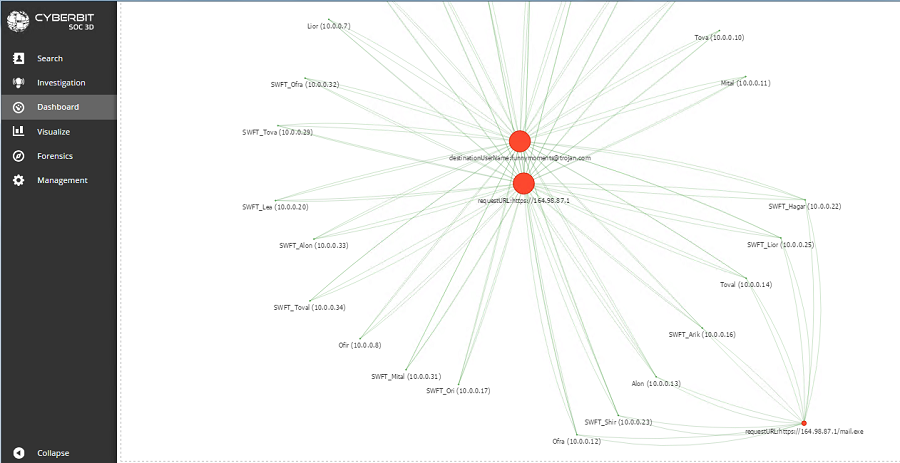
Cybersecurity Investigation – Link Analysis
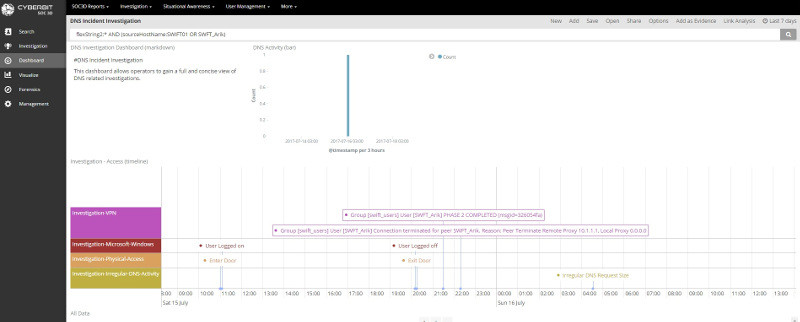
Cybersecurity investigation timeline
So, the next stage in the evolution of the modern SOC is in becoming proactive. Not only to respond but to detect cyber campaigns before they turn into active attacks. In order to get there, we must add an investigation layer to our SOCs, just like the tools and capabilities that are common practice in the Intelligence community such as correlation engines, advanced dashboards, link analysis, BI and timelines. These must become a substantial part of our day-to- day cyber security operations, a necessity that I’m sure that 2 years from now will be a basic capability for every SOC analyst.
We need to enable our SOCs to Automate. Orchestrate. Investigate.
Adi Dar is the CEO of Cyberbit

