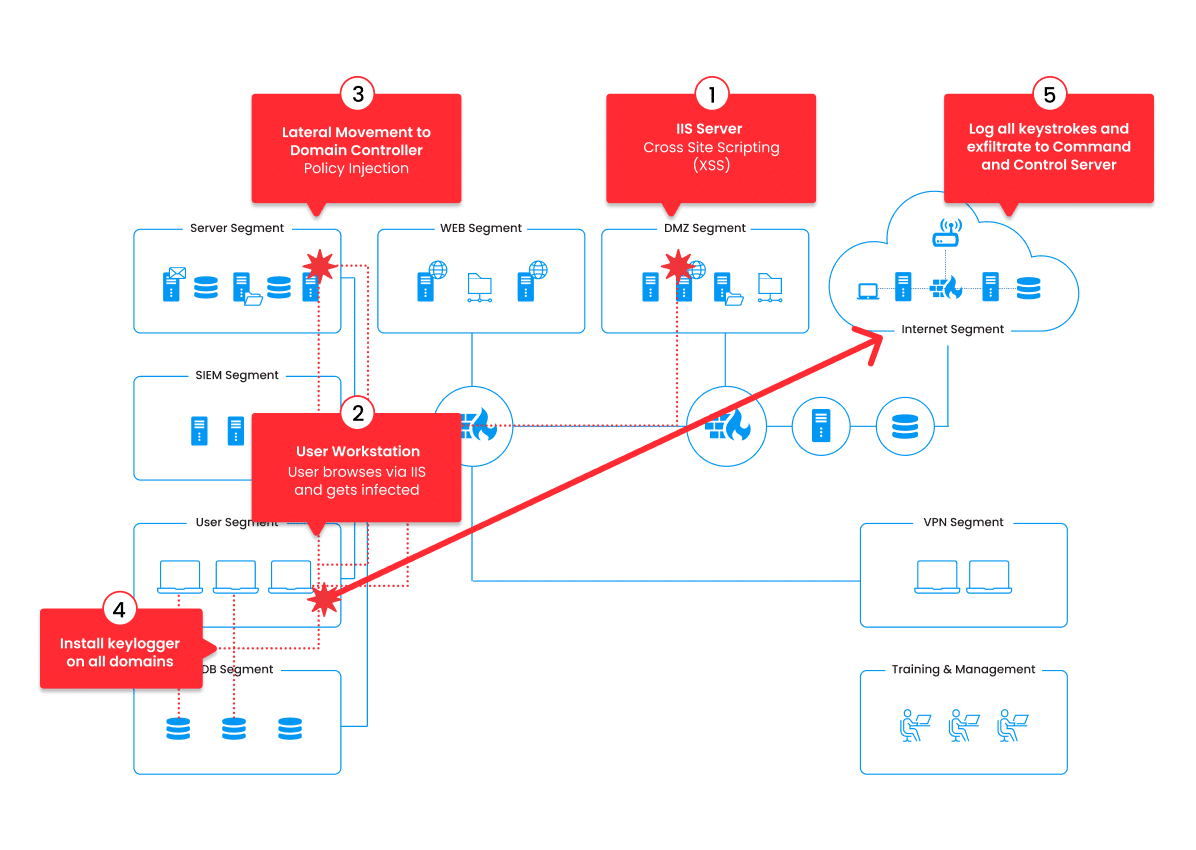
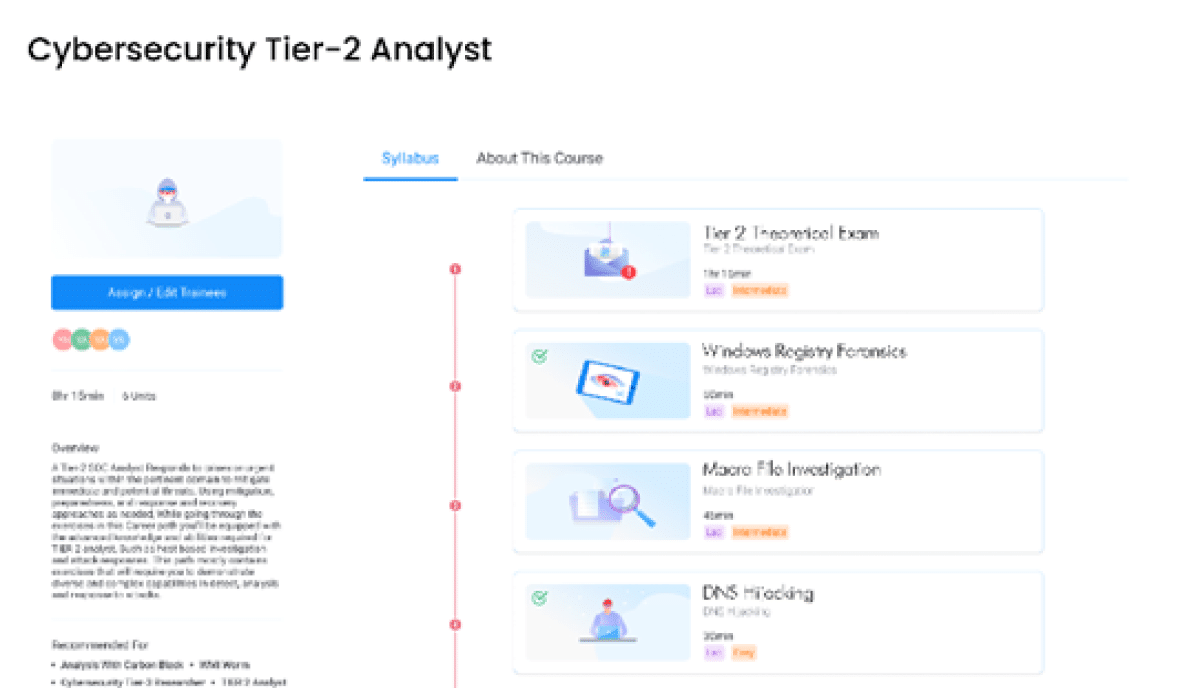
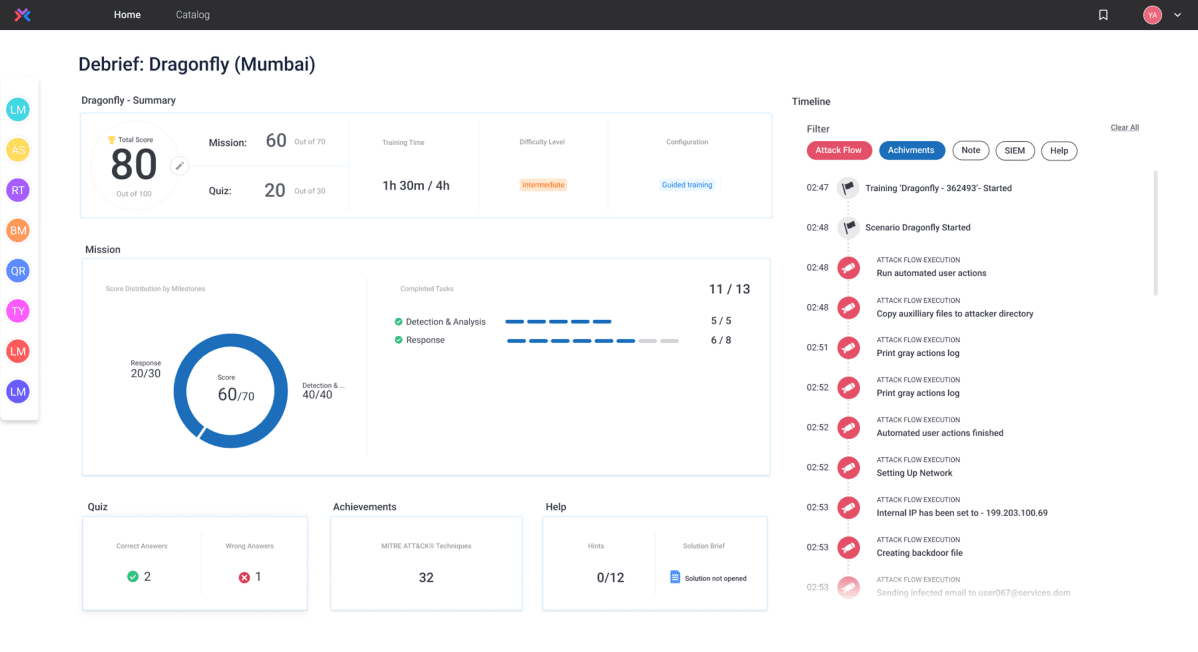
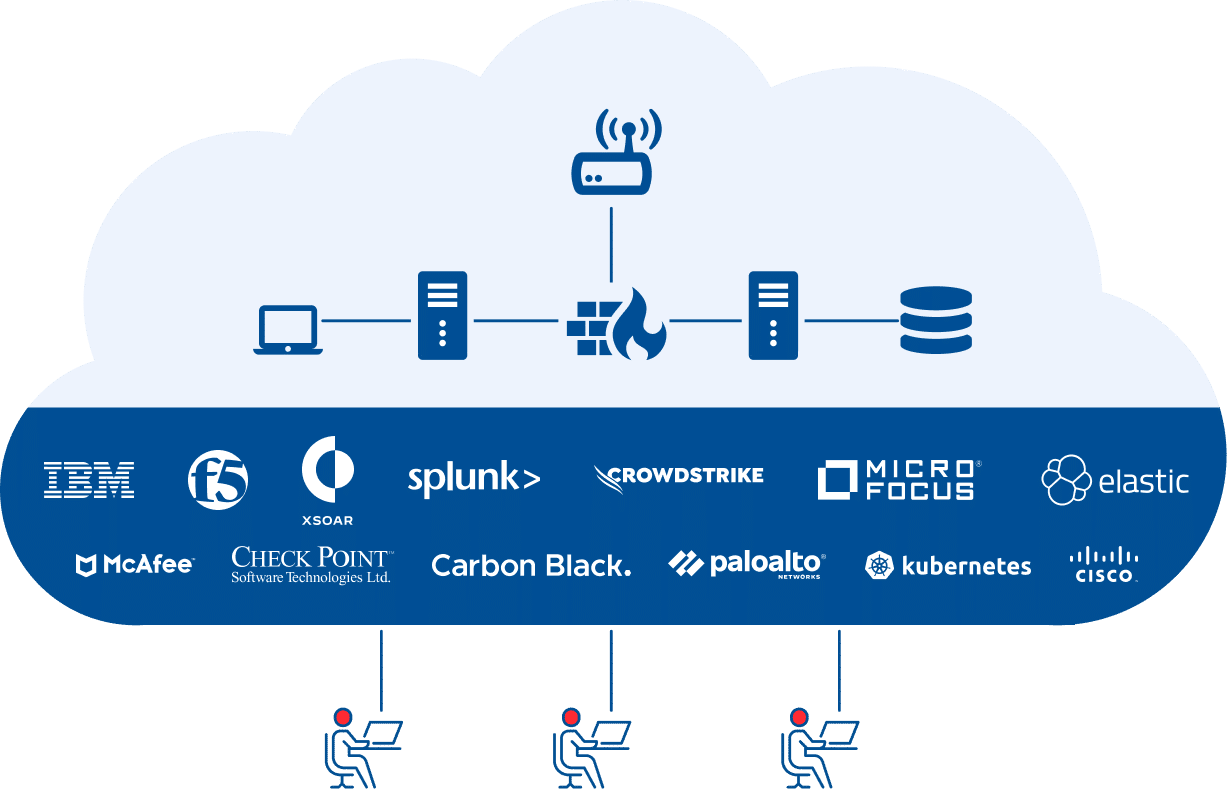
Building an elite cyber defense team means challenging it in live attacks, like the ones that will be encountered on the job, and replicating the entire SOC experience. The Cyberbit platform includes an advanced cyber range that has been perfected over the last 10 years, combining networks, attacks, security tools, and assessment capabilities into a well-orchestrated experience.