As a cybersecurity professional, I am certainly aware of the threat of ransomware attacks. When my dad was hit a few months ago, my parents expected me to be able to easily rescue him from what they saw as just another computer glitch their geeky daughter would be able to take care of, but it turns out there was very little I could do to help.
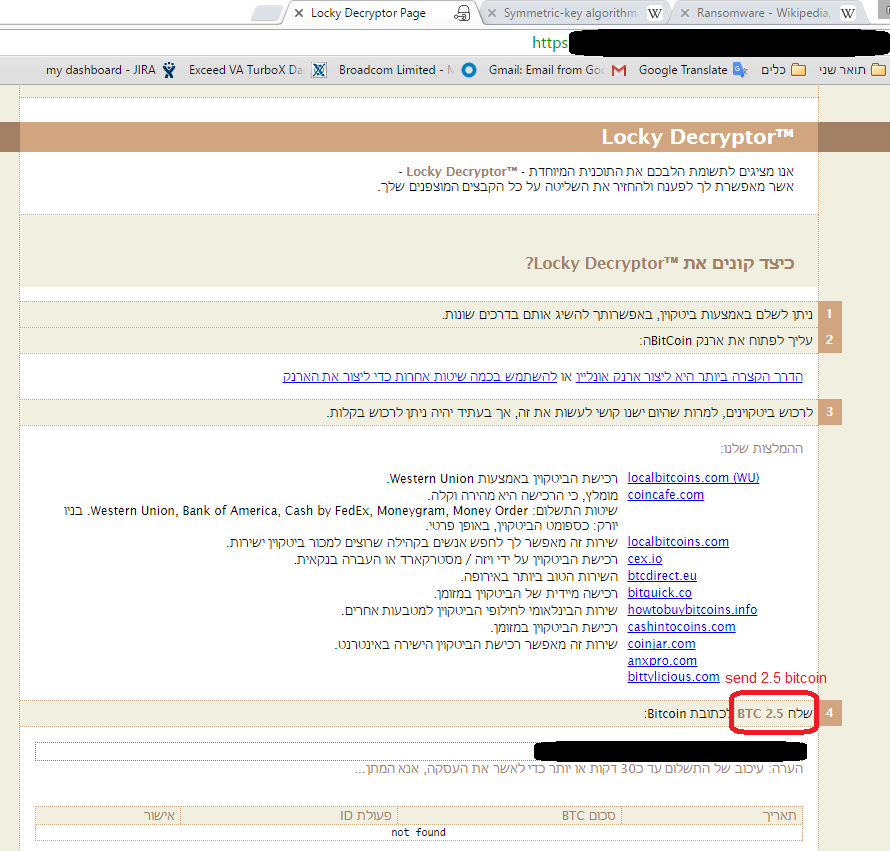
It all started when our family Whatsapp group starting buzzing one Friday morning. My dad had shared a picture of his computer screen showing a ransom note. It was a popup window pointing to a very legitimate looking webpage notice, localized to Hebrew, that presented itself as a legitimate ‘Locky Decryptor’ security product that promised to decrypt and return his files. The program just happens to be ‘sold’ via bitcoin and the price tag was 2.5 bitcoin($2649).
Locky decryptor tool for purchased with bitcoin
No magic cure for ransomware attacks
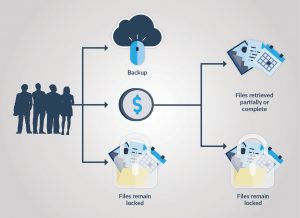
My mother asked me to help dad take care of his latest computer glitch, but the second I saw the note I knew this was far more serious. My dad had been hit by ransomware. Ransomware is a computer malware that “captures” precious files by encrypting them so they cannot be used, and then holds them ransom and demands the owner pay a sum of money via bitcoin to release them. Unfortunately, there is not much that can be done once your computer has been infected with ransomware. You can either pay up or lose your files.
My dad isn’t the type of guy to be bullied. As a tax consultant, he is also diligent about backing up his hard drive. His last backup had been 36 hours before the ransomware attack and he was willing to redo the work rather than pay the criminals. There may be something to his tough, Israeli “never negotiate” attitude. The people behind these attacks are criminals. If he pays up once, they may be back for more. Also, there is no guarantee that once the ransom is paid they will unlock all your files. Though, theoretically, it is in their best interest to smoothly comply and thereby encourage people to keep coughing up the bitcoin.
The FBI agrees with my dad. Cyber Division Assistant Director James Trainor said, “Paying a ransom doesn’t guarantee an organization that it will get its data back—we’ve seen cases where organizations never got a decryption key after having paid the ransom. Paying a ransom not only emboldens current cyber criminals to target more organizations, it also offers an incentive for other criminals to get involved in this type of illegal activity. And finally, by paying a ransom, an organization might inadvertently be funding other illicit activity associated with criminals.”
Ransomware victim response tree
Lucrative cybercrime is growing fast
Ransomware is estimated to be the second-largest attack type according to Verizon’s 2016 Data Breach Investigation Report. It started with small scale ransomware attacks on private citizens, like my dad. Home PCs are easy targets because private citizens don’t usually invest in top of the line security products. We are all essentially sitting ducks. Each ransomware attack demands a relatively small amount of money such that many people would just choose to make the payoff and get back to business as usual. My dad’s assessment of these criminals as ‘bullies’ is pretty accurate. Ransomware is very easy to create, with ransomware kits available for purchase on the darknet. Almost no advanced computer skills required. The Israeli National Cyber Bureau announced March 20, 2017, that Israel ranks 29th globally for the number of ransomware attacks, averaging 130 attacks per month, each time extracting an average of $722. First place goes to the USA where over $160 million was extracted in 2016 (Metadata Consulting).
Ransomware goes corporate
Success never goes unnoticed, and organized crime has caught wind of ransomware and taken it up a notch, now targeting high value corporate and government organizations where the payoffs are much higher. For large organizations, the cost of losing access to important data can be tens of thousands of dollars per hour. Enterprises also have access to more cash so they can be squeezed to fork over very large sums fast. Some are even stockpiling bitcoin ahead of time as part of their incidence response planning. The FBI’s Internet Crime Complaint Center (IC3) confirmed that in 2016 there was a significant increase in ransomware attacks targeting various sectors including healthcare, retail and critical infrastructures such as energy and utilities. Cybersecurity Ventures and Herjavec Group estimate the total global damage for 2016 to have reached $1 billion.
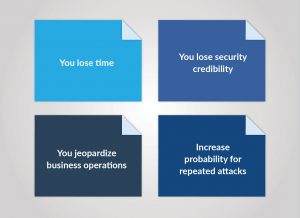
Large enterprises face additional risks when ransomware strikes. Disruption of service will be noticed by customers and the press causing damage to the organization’s security credibility and overall brand reputation. ‘Ransom’ is not an expenditure investors or board members want to see on the balance sheet. Furthermore, paying up once may increase the probability cyber criminals will strike again.
Organizational costs of ransomware attacks
Common ransomware infection methods
• Phishing – malicious emails that use human engineering tactics to trick users into opening them and clicking on links to sites where malware code is downloaded
• Drive-by download – malicious websites (or innocent sites that have been hacked) that inject malicious code on to user PCs via the web browser
• Malvertising – weakness in online advertising networks are exploited to push ransomware code to users via ads
Some ransomware software uses an encryption key and therefore requires communication to the command and control center. In this case, communication monitoring security solutions can be effective at detecting it. But more and more ransomware is being designed to outsmart communication monitoring by working in offline mode without the need to retrieve an encryption key from the command and control attack server. They simply include the key within the malware code so no communication is needed. Cyber criminals have also found a way to victimize individuals and organizations that keep a stellar backup routine by including code that erases backups. Newer ransomware variants also delete Shadow Copy, so relying on Microsoft for restoration will not protect you from data loss. Sophisticated attacks targeting organizations may include mechanisms to reach files stored on the shared network, looking for directory and file names that are likely to contain highly sensitive information.
Ransomware evades detection by security tools
Just like biological viruses, malware adapts to evade prevention tools. Here are some common technologies employed by vendor security tools and how ransomware code developers circumvent them.
• Sandboxing and virtual machines –Security products often use virtual machines (VMs) or sandboxes to execute and analyze potentially malicious code in a safe environment before it is approved to enter the organizational network. Malware authors often design code to detect isolated environments and prevent the malicious code from running when inside an isolated environment to avoid detection. Read more: Anti-VM and Anti-Sandbox Explained
• Signature-based detection – relies on vendor researchers quickly identifying new malware variants and distributing signatures or hashes to block them. The problem is that this still gives the hackers hours or even days to spread malware unfettered until a signature is distributed. Considering how easy it is to slightly alter malware binary and recompile it, this technique will always leave a window of opportunity open to new ransomware variants. Furthermore, 70-90% of malware attacks are custom targeted at a specific enterprise or individual. Hackers design and modify the malware significantly or even develop new code from scratch so they cannot be detected by indicators of compromise (IOCs) or signature-based detection tools.
Protecting against ransomware
What can private citizens and enterprises do to protect themselves? Be prepared, take defensive steps and have a response plan ready.
• Security awareness and training – make sure every employee has seen samples of real phishing email, malicious links and knows how to avoid becoming an unwitting victim
• Ransomware prevention systems – ransomware often bypasses antivirus systems, but advanced endpoint detection systems can identify the unique characteristics of a ransomware attack, block and initiate backup processes to prevent the need to even consider making a ransom payment
• Automatic backups – the longer it has been since your last backup, the greater the damage
• Have a plan – Ransomware is real and everyone is likely to be targeted. Prepare a response plan ahead of time so that you can make critical response decisions before the pressure is on. Consider what happens if you choose to pay? Should you consider paying at all and under which circumstances. Remember that the FBI and other law enforcement agencies discourage making payoffs as it encourages criminals, may lead to repeated attacks and there is no guarantee you will get a decryption key to all your ransomed data after payment is made. Furthermore, making a payoff to criminals can be even more damaging to company reputation than downtime.
Sharon Sharlin is Product Marketing Manager at Cyberbit