While rolling out Cyberbit’s Endpoint Detection and Response (EDR) in an international airport in Europe, our researchers identified an interesting crypto mining infection, where cryptocurrency mining software was installed on more than 50% of the airport’s workstations. The findings raise concerns regarding the ease of installing malicious software within corporate networks despite being protected by antivirus systems.
How we have detected the crypto-mining software
The malware was discovered while rolling out Cyberbit EDR, an advanced behavioral detection and threat hunting platform, in an international airport in Europe. Based on further analysis we can associate this malware with the anti-coinminer campaign reported by Zscaler in August 2018.
During a standard rollout process, we install our kernel-level EDR Agents on the customer’s workstations. The Agent collects endpoint activity and the data is centralized in a big-data repository where it is analyzed using a set of behavioral algorithms. The behavioral engine then generates alerts for endpoint behaviors that are potentially malicious. Cyberbit’s team of analysts examines these alerts and whitelists legitimate processes. This enables our customers to achieve accurate detection of evasive activity, which often bypasses antivirus systems, while minimizing false positives during ongoing operation after rollout.
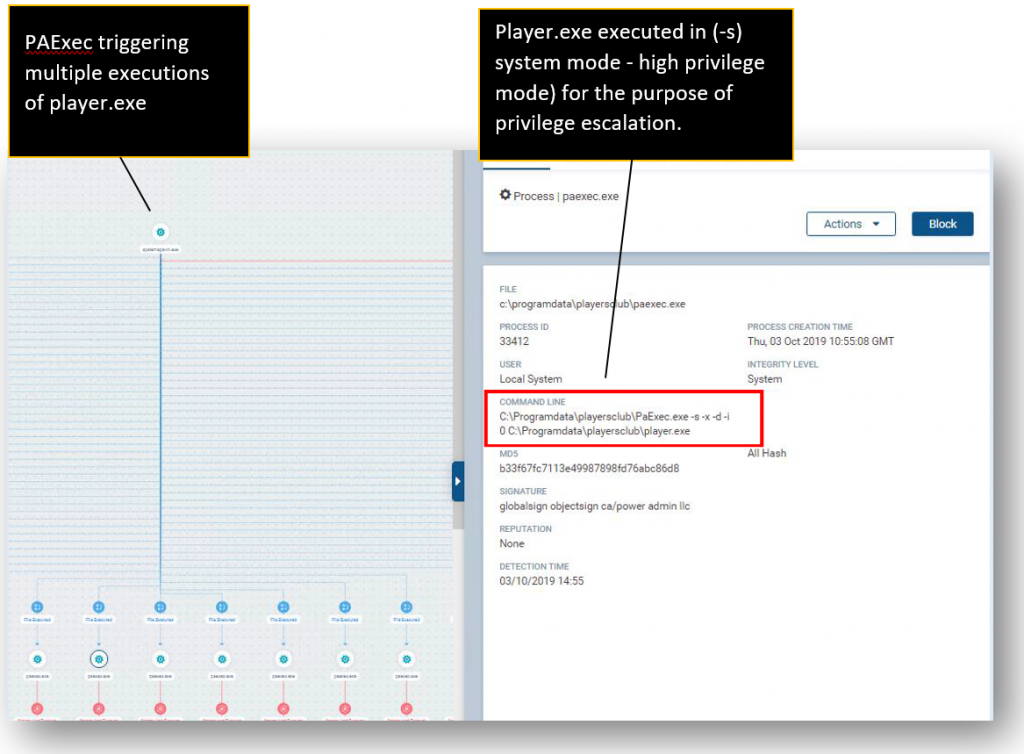
During this process, our behavioral engine alerted on suspicious use of the PAExec tool. The tool was used multiple times over a short period to launch an application named player.exe. PAExec is a redistributable version of Microsoft’s PSExec, used for running Windows programs on remote systems without having to physically install software on these systems. The use of PAExec is often an indication of malicious activity, moreover the repeated use of the tool.
Cyberbit EDR analysis screen shot:
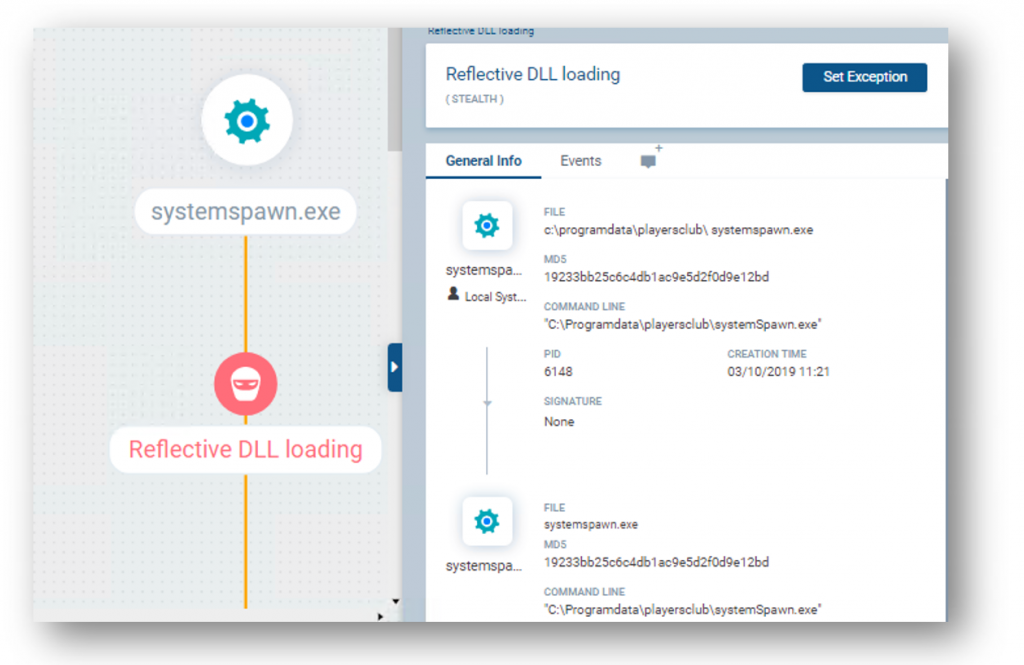
In addition, our behavioral analysis engine detected the use of Reflective DLL Loading after running player.exe. This is a technique for remotely injecting a DLL into a process without using the Windows loader, avoiding accessing the hard drive. Reflective DLL loading is a typical defense evasion tactic used by attackers to mask the loading of malicious files.
The malware may have been used for months prior to the installation of Cyberbit EDR, although all workstations were equipped with an industry standard antivirus.
The combination of the 2 suspicious behaviors triggered a high priority EDR alert which we proceeded to investigate.
Cyberbit EDR analysis screen shot: Reflective DLL Loading Alert
Analysis and additional findings
Once we have received the alert, we analyzed the chain of events by using EDR behavioral graph analysis. The malware was suspected to be a Bitcoin miner because of its behavior of executing multiple processes over a short timeframe, typical to a miner using system resources for its calculations. We have cross- checked our behavioral findings with VirusTotal site for further analysis, to understand its purpose.
- Based on the execution path c:\ProgramData\playersclub\player.exe this malware was associated to CryptoMiner Variant #2 reported by Zscaler – the xmrig miner
- Although over a year has passed since Zscaler reported this malware in August 2018 only 16 out of 73 detection products on VirusTotal were able to detect the file as malicious.
VirusTotal Report
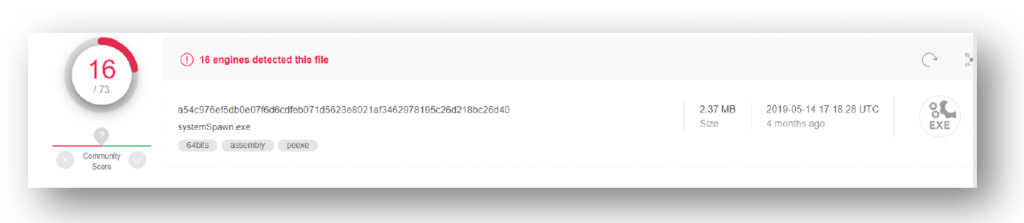
- Based on the above info the file was confirmed as a the xmrig Monero miner.
- PAExec was exploited mainly for the purpose of privilege escalation. This can be observed in the EDR screen shot showing the malware being executed in system mode (the -s attribute). System mode provides maximum privileges, so the miner would take priority over any other application for the use of workstation resources. This impacts the performance of other applications, as well as that of the airport facility. The use of administrative privileges also reduces the ability for security tools to detect the activity.
- Player.exe used Reflective DLL Loading to load additional DLLs from memory for the Cryptocurrency miner. This tactic allowed it to evade detection as the file is not fetched from the hard drive and would not go through file-based detection systems like AV and most NGAV systems.
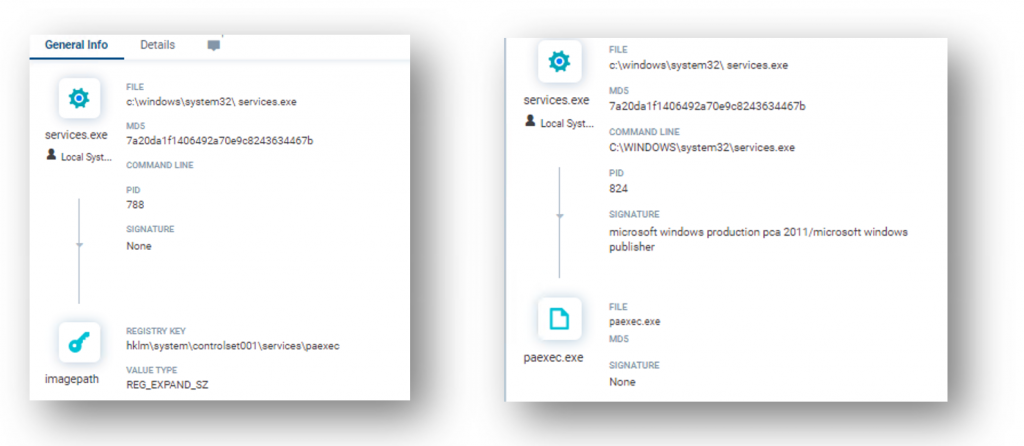
- The malware added PAExec.exe to the registry thereby achieving persistence.
Persistence Mechanism: Cyberbit EDR Screen Shot
- All workstations in the airport ran an industry standard AV solution, which did not detect the malicious activity.
- We are not able to assess how the malware got into the workstations in the first place as this happened before our EDR was installed.
- The time from setting up EDR to detecting the malicious activity was approx. 4 hours.
Remediation
We used Cyberbit EDR threat hunting tool to search for the MD5 across the airport network and found the malware residing on over 50% of the workstations, while not running at that time. We’ve removed the malware from the organization’s endpoints and blocked its ability to execute.
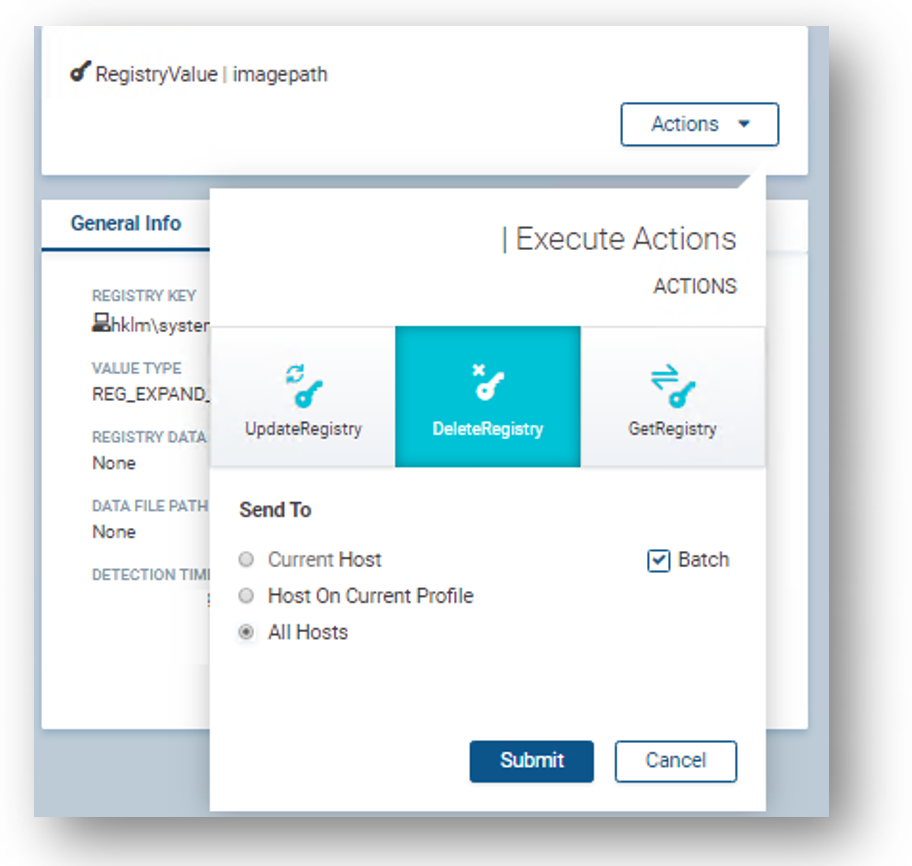
In addition, we’ve used a unique remediation capability to remove malicious entries from the registry. These registry keys were added by the malware to provide persistence. The removal of the malicious keys from the registry ensures that not only is the malware itself blocked, but so is its persistence mechanism.
Remediation – removing the malicious registry from all hosts
EDR Screen Shot
Conclusion
Here are our main takeaways:
- Anti-virus vendors themselves have been decrying the death of Antivirus since at least 2014. Most cybersecurity professionals concur, and this discovery offers a compelling proof point as to why. Despite our customer’s enterprise-wide network AV deployment, the majority of its workstations were infected with malicious software.
- The malware we found was first discovered by Zscaler more than a year ago. It was modified just enough to evade the vast majority of existing signatures for it, with only 16 out of 73 detection products on VirusTotaldetecting the sample as malicious.
- Because the malware happened to be a cryptominer, its business impact was relatively minor, limited to performance degradations leading to quality of service and service interruptions, as well as a significant increase in power consumption throughout the airport.
- In a worst-case scenario, attackers could have breached the IT network as a means to hop onto the airport’s OT network in order to compromise critical operational systems ranging from runway lights to baggage handling machines and the air-train, to name a few of the many standard airport OT systems that could be cyber-sabotaged to cause catastrophic physical damage.
We advise corporate customers not to rely on AV alone. To reach an optimal combination of prevention and detection, we strongly suggest complementing AV with EDR, which uses behavioral analysis (which doesn’t rely on signatures or IoCs). With the increased convergence of IT and OT networks, we strongly urge airports to also ramp up the protection of their OT network, which is used to control physical airport systems. By penetrating OT networks attackers can cause catastrophic physical damage and this should, therefore, be a strategic cyber defense priority.
Meir Brown
Head of Research, Cyberbit

