We are seeing an alarming increase in high profile cyber attacks on banks, specifically in India. According to Proofpoint, nearly 59% of all malicious email payloads in the first quarter of 2018 were banking trojans.
The biggest breach was on the Bangladesh Bank in February 2016, where 101 million dollars were withdrawn from a Bangladesh bank account at the Federal Reserve Bank of New York. The Dridex malware was used for the attack.
Recent cyber attacks on banks in India include:
- February 2018 – The attack on City Union Bank. Cybercriminals hacked into City Union bank SWIFT systems and transferred about 2 million dollars through three unauthorized remittances to lenders overseas.
- August 2018 – The attack on Cosmos Bank. Hackers infiltrated the bank’s ATM server, installed a malware on it and stole credit card information of customers with SWIFT codes. The attack was carried out in two phases. In the first phase, 11.5 million dollars were stolen through transactions from multiple countries. In the second phase on the same day, about 2 million dollars were transferred through debit card transactions across India.
- October 2018 – The Mumbai branch of the State Bank of Mauritius was hit by a cyber-attack through a fraudulent SWIFT payment. About 14 million dollars were stolen.
The actors behind the cyber attacks on banks
The US-CERT has published reports tying the North-Korean group, HIDDEN COBRA, to cyber attacks on banks in Asia and Africa. Securonix published a report on the attack on the Cosmos bank, tying the exploitation methods leveraged in the Cosmos bank to the US-CERT report above. The motivation of the North Korean hacker group is obviously financial. Sanctioned countries like North Korea have built cybercrime capabilities to illicitly secure funds from abroad.
Attack methods
The basic components which are usually compromised in cyber attacks on banks are the SWITCH and SWIFT systems. SWITCH are servers which are responsible for sending corresponding approval request from the ATM to the core banking system for approval. SWIFT is a global provider of a secure inter-banking messaging system used to communicate between banks to electronically wire funds between accounts. The SWITCH and SWIFT are the most sensitive components of a bank infrastructure, as they are responsible for the authorization process of funds transfers.
The Lazarus group utilizes various tactics to infiltrate the bank’s infrastructure and compromise the servers:
- Customized Spear phishing emails with weaponized attached documents
- Custom payloads, packers and utilizing advanced anti-VM/Sandbox techniques – This was done in almost all bank heists to avoid static analysis and sandbox products in the Cosmos bank attack the Themida packer, which is considered as one of the most high-end packers, was used.
- Multi-stage droppers with an ability to download and execute shellcode reflectively in memory – in the Cosmos bank some samples were run reflectively in memory to avoid writing the samples to disk.
- Advanced data collection tools/scanning tools to map the target organization –Backdoor.Contopee which was used in the Philippines bank heist for this purpose. Also, the Bankshot malware had a wide array of scanning capabilities to gather network addresses and collect information on the local file system.
- Lateral movement tactics which involve using of legitimate credentials – In some samples, we have seen the adversary utilizing administrative default shared folders such as C$ and D$ to write the payload and later execute it using scheduled task. This behavior was detected as part of the Taiwan heist campaign using the Bitsran loader/spreader.
- Malicious proxy applications. An example is the NukeSped variant reported in the FastCash related campaign. A proxy server communicates with other compromised hosts and forwards the request to the external operator, hence reducing the exposure of the malware and enabling bridging over segmented subnets.
- Compromised Switch application servers to intercept financial request messages and reply with fraudulent response messages – according to the us-cert this was done in the Cosmos bank heist using compromised IBM IAX servers.
- SWIFT environment compromise. In the Bangladesh bank heist the Trojan-Banker.Win32.Alreay was used, according to this report, in order to compromise the oracle db on the swift application server and generate fraudulent switch inter-banking transfer requests to multiple banks.
- Erase event logs and prefetch files to cover up their tracks.
- Erase transaction reports. In the Bangladesh heist, the adversary intercepted printed transaction reports to bypass manual audit.
Which vulnerabilities make cyber attacks on banks possible?
Weak endpoint security – The lack of advanced security products to detect sophisticated malicious behavior instead of relying on AV signatures which were rendered useless due to packing and utilization of custom payloads.
Long patching process (Flash vulnerability) – In The Hidden Cobra attack against the Turkish financial sector, a spear-phishing email with a document exploiting a vulnerability in Adobe Flash was used. The malware was successfully downloaded by using masquerading techniques such as encrypted strings, dynamically loading APIs, process injection and more.
Lack of security awareness – Social engineering techniques to lure employees into clicking malicious links and opening malicious documents. One example is the cyber attack on banks in Latin America during 2017 using malicious document masquerading as a tax income document:
Source: Securing Tomorrow, McAfee blog
Weak Internal audit controls – The movement of money between accounts, especially between countries, needs to be closely monitored and controlled.
In the TPBank Case, the network was compromised and hackers managed to send commands to transfer funds, but internal anti-fraud controls detected and stopped the transfer before money was lost. This is a powerful example of how the entire organization must be a part of the security mindset.
Steps to Protect Against Cyber Attacks on Banks
- Organizations in India, and other high-risk countries can clearly improve their posture by using more focused monitoring of critical transaction servers, and by using improved detection technologies.
- Adopt an “already breached” mindset and internalize the fact that no matter how good their cyber defenses are (and they need to be very good), hackers will always find flaws. Therefore, security needs to also focus on threat detection.
- Anti-fraud is a layer of cybersecurity
- Threat hunting – Both technologies and expertise. Need to be able to constantly receive feeds of IOCs and pro-actively hunt similar threats inside your organization (bank). This requires both advanced threat hunting tools and training for the security team.
- Segmentation with good filters between the sub-segments (firewall, IPSs, others)
- Automate as much as possible with SOAR (Security Automation and Orchestration) technology.
Cyberbit SOC 3D is the first Security Automation and Orchestration (SOAR) platform combining automation, orchestration, and big-data powered investigation into a single and comprehensive incident response platform that triples SOC efficiency, provides unprecedented visibility and reduces time-to-respond by 90%.
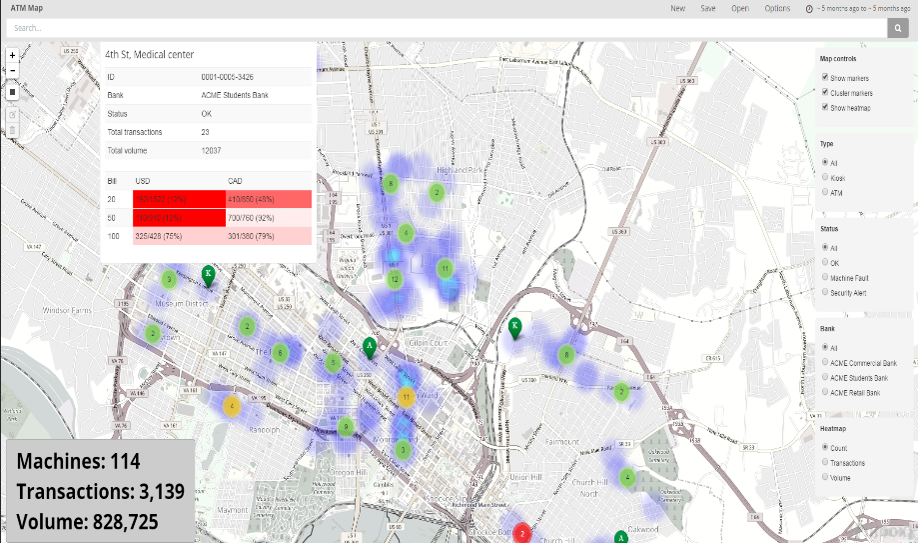
SOC 3D ATM Dashboard
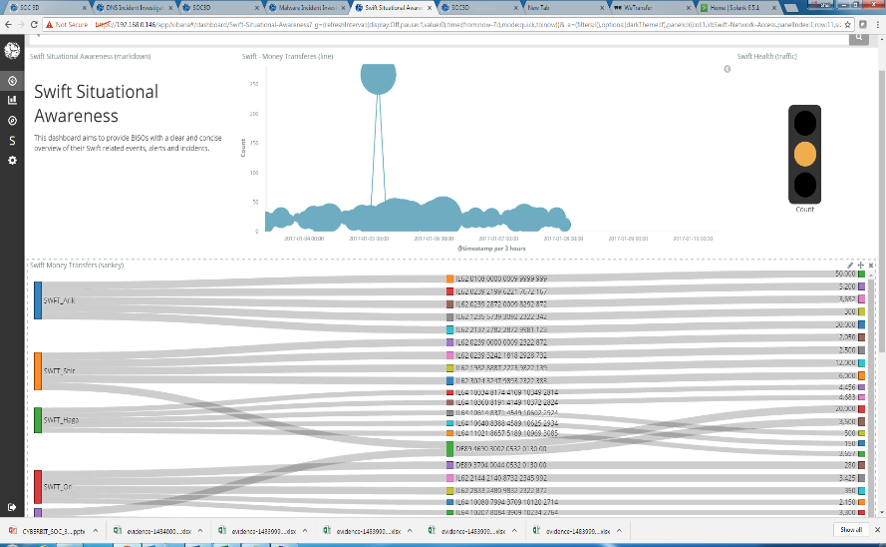
SOC 3D SWIFT Monitoring Dashboard
Hod Gavriel is a Malware Analyst at Cyberbit.
Meir Brown is Director of Research for EDR at Cyberbit
Watch FREE webcast How to Prevent the Next Financial Cyberattack with Next-Gen Technology


