Several researchers have noticed that Dridex does not guarantee its own persistency until it absolutely has to, just a moment before shutdown. This tactic allows Dridex to hardly leave any footprint on the file system and registry, making it harder to detect and remove. How does it do it?
In Windows, every window has a Window Procedure. The Window Procedure is a function that is called in every event that occurs in the system in order to let the window respond to the event. For example, when the system is shutting down, it sends a message to all open windows so they can save their work.
Dridex uses this mechanism for its persistency. After injecting its malicious code into Explorer’s process, Dridex replaces the Window Procedure of Explorer with its own malicious function. This is achieved by calling the SetWindowsLong WinAPI function. For every message the malicious function receives it calls the original function, except for the messages WM_QUERYENDSESSION and WM_ENDSESSION. These messages are sent when the system is shutting down. Once one of them is received, Dridex knows that the system is shutting down and that it should write itself into the registry autorun key, in order to make sure it is executed again when the computer is restarted.
The malicious Window Procedure function is shown here:
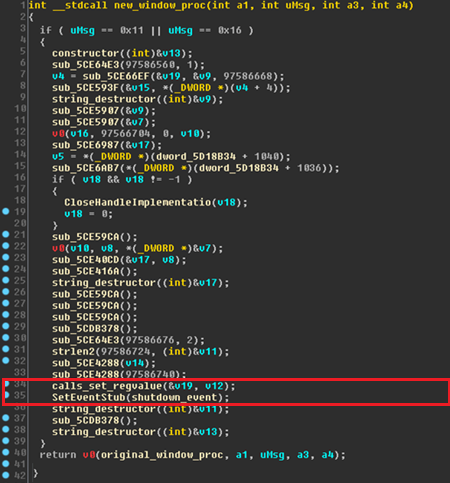
When the computer is restarted, Explorer reads the autorun registry keys and runs the programs they specify. One of the first things that Dridex’s malware does when running is to delete its autorun key and the executable file that contains its code. The malicious code is again injected into Explorer, and now resides in memory alone.
Looking at the actions Dridex performs just before shutdown and immediately after startup, we can conclude that Dridex’s traces on the disk and registry exist only for a very short period of time, in a timeframe which is also harder to monitor.
A full report of Dridex malware can be found here.

