WannaCry, WannaCryptor and Wana Decryptor are three of the common pseudonyms for Friday’s massive NHS ransomware attacks on the UK’s national healthcare system. As the UK gets ready to return to work Monday morning experts are still very concerned about the continued outbreak and are busy trying to help get computers up and running again smoothly.
Latest estimates are that the NHS ransomware attack has impacted 200,000 machines in 150 countries. The ransomware has also spread to other types of organizations outside of healthcare such as FedEx, Renault, Spanish Telecom company Telefonica and the Russian interior ministry. The malware itself does not appear to have been designed specially to target the healthcare system, but healthcare systems and hospitals are being targeted and affected for three main reasons.
Why did the NHS ransomware attack hit healthcare institutions and hospitals?
1) Data is critical
We are all living in the digital age, but in healthcare access to vital data can literally be a matter of life and death (or malpractice lawsuit). Hospitals and healthcare providers gather and store massive amounts of medical history data about each and every one of us. Without access to medical records, test results and other information modern medicine screeches to a halt. Hospitals also carry out clinical research. The latest NHS ransomware attack severely impacted hospitals across the UK, many of them forced to cancel non-urgent surgeries and divert ambulances from reaching their emergency rooms. Medical teams reverted back to pen and paper to do patient intakes, diagnosis and manage treatment. Ransomware attackers look for victims who have a lot to lose and will, therefore, be highly motivated to be ‘easy victims’ and quickly make payments.
2) Systems are vulnerable
Hospitals and healthcare providers like the NHS tend to have large, sprawling computer networks. There can be a wide variety of operating systems installed on workstations and servers, some of them quite old. This kind of network is very difficult to keep updated with all the latest vendor security patches. It’s an IT security nightmare. If a hacker sets his or her sites on penetrating a hospital network, in most cases an entry point will be relatively easy to find.
3) Access to cash
When we think of who has access to large amounts of cash, banks, credit card companies and billionaires come to mind. But financial institutions and extremely wealthy people tend to take guarding their money and privacy pretty seriously and have the best, most advanced technologies and procedures in place. Healthcare systems have access to cash, running a hospital is an expensive business and requires very large sums of money.
All this means that when the ransom notes pop up on terminals, the most likely decision will be to pay up.
How WannaCry (Wanna Decrypt0r) ransomware works
The virus that hit NHS last week was delivered as via a phishing email that tricks users into clicking on a link, which then downloads a Trojan. Once the ransomware payload is executed, it encrypts files on the computer’s hard drive, deletes the originals and displays the following message, requesting the user to pay a ransom in order to decrypt and recover the files.
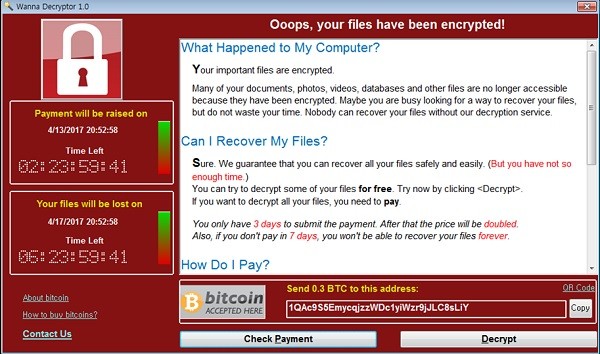
NHS Ransomware note demanding payment of 0.3 Bitcoin (approx $325)
5 anti-ransomware actions for healthcare providers:
1) Patch Windows XP machines
2) Disable SMBv1 in Windows and block it in your firewall.
3) Deploy Windows patch MS17-010
4) Use an Endpoint Detection and Response Product with anti-ransomware capabilities
5) Refresh and practice security awareness for all employees
Further reading:
WannaCryptor Ransomware – 3 Actions You Should Take Immediately
Get Cyber Security Awareness Right in 2017
Tal Morgenstern is Head of R&D, Endpoint Detection and Response Team at Cyberbit

