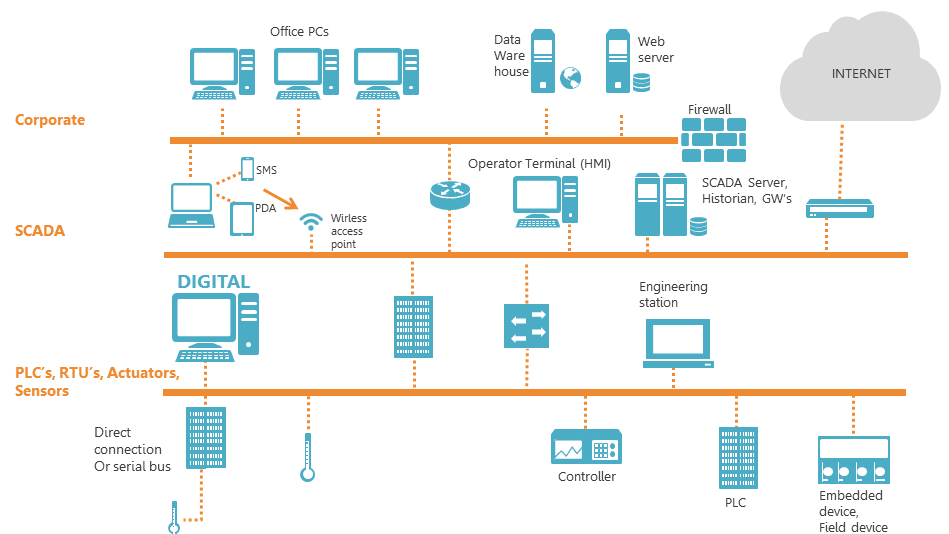
Industrial Control Systems (ICS) are the backbone of the global economy. ICS solutions control the operational technology (OT) networks that run large-scale manufacturing facilities, critical infrastructure sites, and many more of the building blocks of modern society. Therefore, ICS network security is critical to the economy.
The OT networks running manufacturing and critical infrastructure facilities are highly-complex and dynamic, including a broad range of processes, policies, services, and protocols. They also include many assets from multiple vendors – some of which may date back 20-30 years and run old, proprietary protocols which are not even IP-based.
Because of this diverse ecosystem, the legacy solutions that control large-scale OT networks are challenged to provide visibility into exact network structure – or even discover exactly which assets from which vendors are implemented. This ICS network security blind spot leaves OT networks highly-vulnerable to targeted attacks, malware, and other cyber threats. To gain the upper hand on would be cyber attackers, be they financially or politically motivated, ICS network managers are seeking out automation technologies to make threat detection and remediation fast, accurate and efficient.
Here are three crucial things you should be automating to meet the challenges of ensuring the highest level of ICS network security: assessment, alerts, and monitoring.
Assessment – ICS Network Security
Knowledge is power, and the first step to ICS network security is knowing your network intimately. Traditionally, a full ICS network security assessment was a lengthy and labor-intensive undertaking that involved interviewing engineers and staff one-by-one and visiting multiple sites to observe and document infrastructure. An automated comprehensive network assessment can be completed within just a few days and will help you quickly grasp the network overall, identify gaps in network architecture and prioritize Risks and recommendations.
Automated ICS Network Security Assessment
Alerts – ICS Network Security
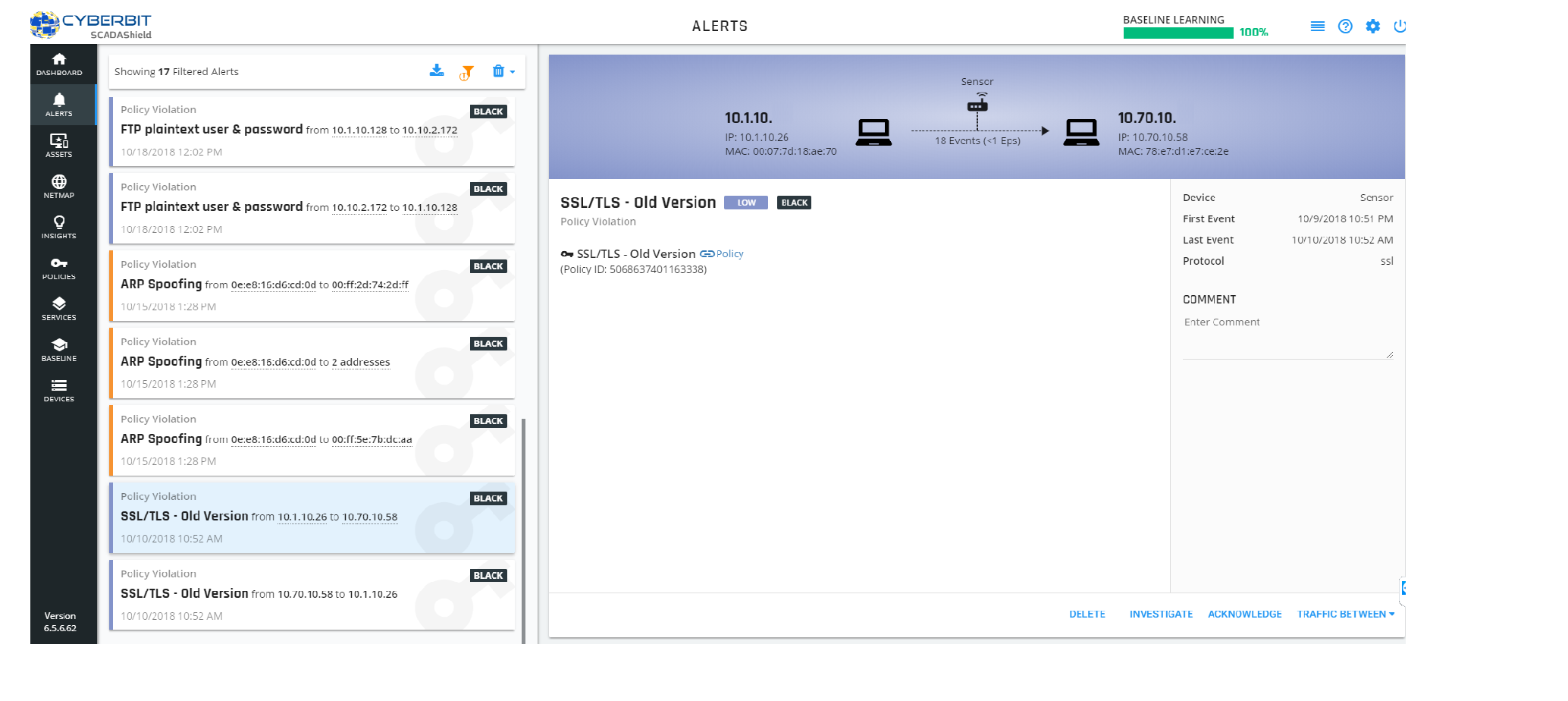
By properly implementing ICS network security policies, procedures and monitoring, manufacturers and critical infrastructure managers increase ICS network security, performance and reliability. Implementation should include procurement, configuration, installation, testing, and start-up – to get the network up and running quickly and minimize future issues. Any deviation from the ICS network security policies should generate automatic alerts.
ICS Network Security Policies Generate Automatic Alerts
Monitoring – ICS Network Security
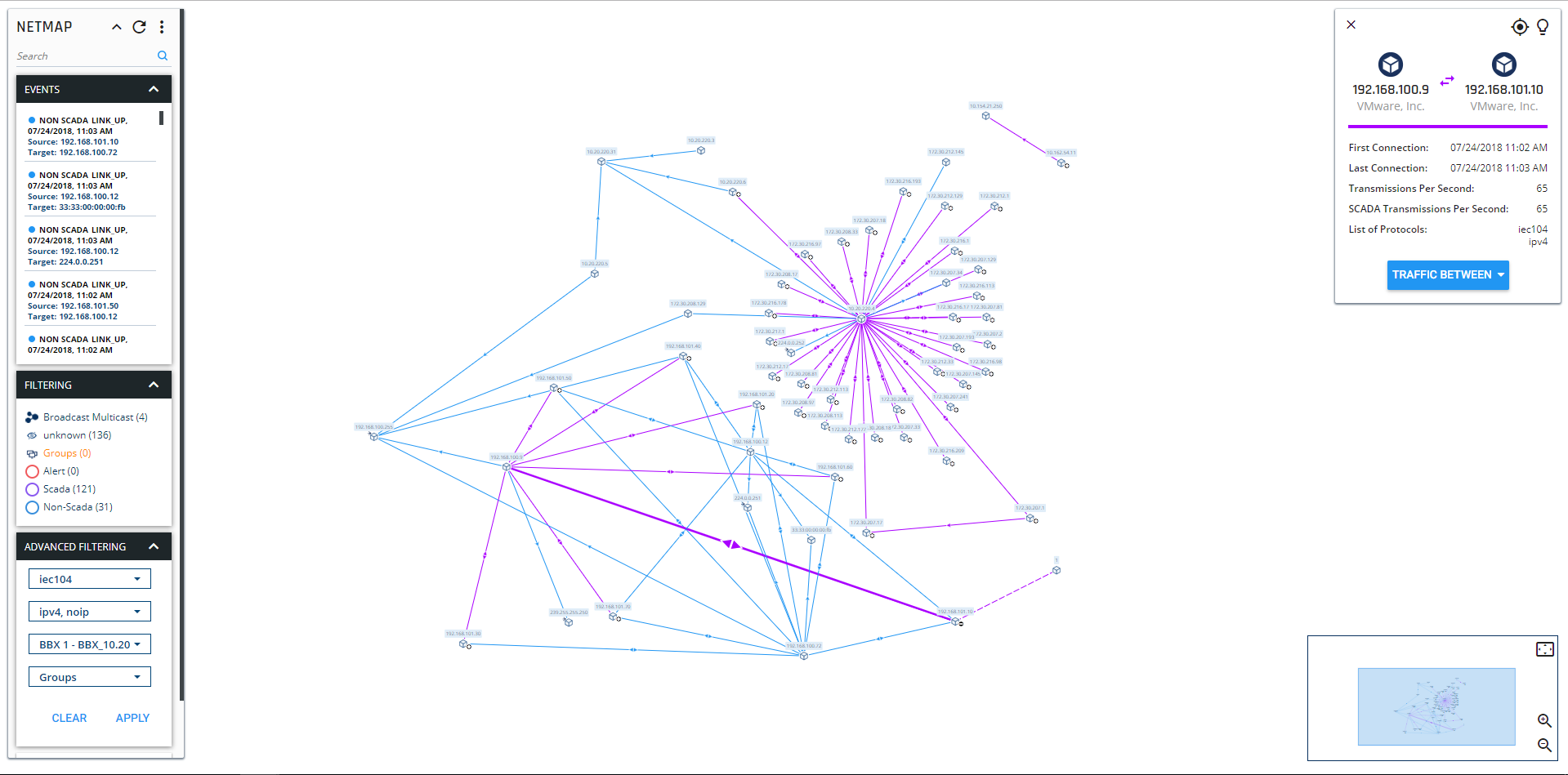
Today’s sophisticated ICS network monitoring technologies can alleviate the burden of ongoing monitoring and maintenance. These solutions monitor key facility parameters and provide a secure environment with wide communication visibility over assets – enabling remediation of issues before they impact production. This enables manufacturers to speed the integration of new equipment and systems while keeping operations at peak performance.
ICS Network Security Monitoring
To learn more about ICS network security, visibility and continuity solutions download: 5 Crucial Steps to Secure Industrial Networks
Ronen Rabinovich is Product Manager for Cyberbit SCADAShield.