SCADA (Supervisory Control And Data Acquisition) networks serve as the backbone for many manufacturing and critical infrastructure industries, including utilities, telecom, transportation and food distribution, performing vital tasks such as monitoring data from pumps, valves and transmitters. Dating back to the 1960’s, these systems were built to provide plant workers with a user-friendly interface from which to gather and analyze data. Still in wide use today, users can view their processes in real-time and when a situation at the plant or on an endpoint becomes dangerous or unstable, a warning alert sounds. They are cost-effective, scalable, easy-to-operate and repair solutions for businesses of any size that need to monitor processes. The open and easy networks are also susceptible to many SCADA vulnerabilities and wide open to cyber attacks.
When the systems were first introduced, each was built upon its own proprietary protocols, with its own firmware, software, authentication methods and interoperability standards. These legacy systems were not built with security in mind and are still in use today despite efforts to standardize – and their inconsistencies create SCADA vulnerabilities that can be exploited. As the industry adopts modern network technology on top of these legacy systems, the situation becomes all the more exploitable.
Although it’s only recently that attackers have come to see the potentially crippling results of striking manufacturing and ICS, it’s now a major concern for businesses and governments around the world. From Stuxnet to the more common reports of attacks on power grids and plants emerging with growing regularity, the reality of SCADA vulnerabilities creates great cause for apprehension.
SCADA Vulnerability: The Common Industrial Protocol (CIP)
SCADA networks use rules for data transfer, referred to as protocols, allowing devices to communicate with each other. If one device uses a different protocol from another one, they will be unable to communicate or share data. The lack of common protocol was an early problem in SCADA systems, so new protocols were developed to unify communication and to provide interoperability between devices.
The Common Industrial Protocol (CIP), developed by Rockwell Automation and now maintained by ODVA, is one of these protocols that aims to unify data transfer. Its many benefits makes it a preferred choice for data transfer and is used in thousands of products by hundreds of vendors across verticals as diverse as car manufacturers and medical devices. It’s not proprietary, making interoperability an achievable reality and helps minimize the costs involved with installation and engineering. It provides common control services with a set standard of messaging services; It allows devices to connect to any network and to configure and collect data from any network; Its common routing capabilities save time and effort during configuration, as no routing tables are needed; and its common base knowledge reduces the amount of training needed when moving between networks.
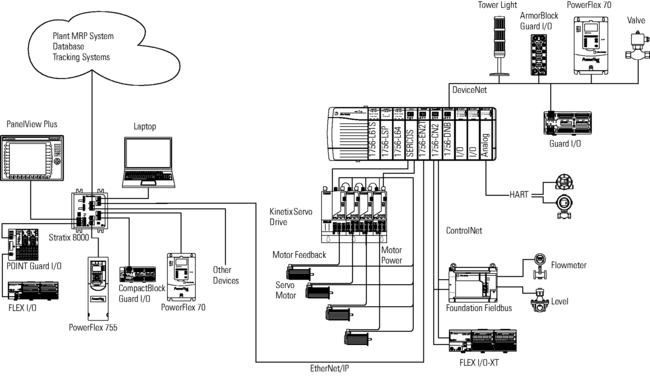
Image source
CIP SCADA Vulnerabilities
But CIP, like all other protocols, comes along with its own SCADA vulnerabilities as well. In 2012 researchers discovered many vulnerabilities in Rockwell’s ControlLogix PLC that could be remotely exploited to enable man-in-the-middle attacks, DDoS attacks, improper access control, validation, and authentication attacks, as well as information exposure attacks. According to The Department of Homeland Security, attacks such as these can result in loss of confidentiality, integrity and availability of devices. The vulnerabilities, for which exploits are already publically available, effect devices used in various verticals including food, water, chemicals and manufacturing.
The software has its own built-in security tool, the Logix CPU Security Tool, but all attacks performed were carried out in the “secured” state.
Here is a look at some of the vulnerabilities researchers found:
Network Monitoring and Lack of Encryption Vulnerability
By downloading Rockwell’s software and monitoring the network traffic, researchers were able to analyze and extract packets to monitor and control the PLC, and therefore obtain information about the processes running on the CPU. Thus they were able to see that passwords were being sent in the packet in plain text.
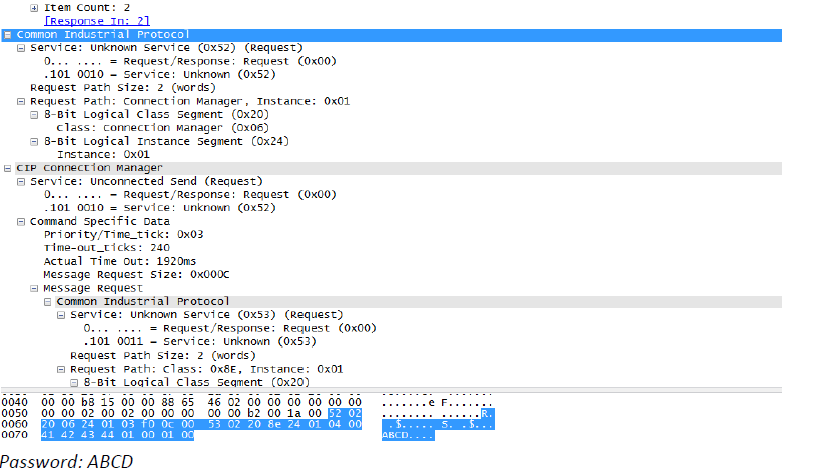
SCADA Vulnerability – Forcing a CPU Stop
The affected device receives a valid CIP message from an unauthorized source, leaving the CPU in a “major recoverable fault” state. The results can be a loss of availability or any other disruption of data transfer with other connected devices.
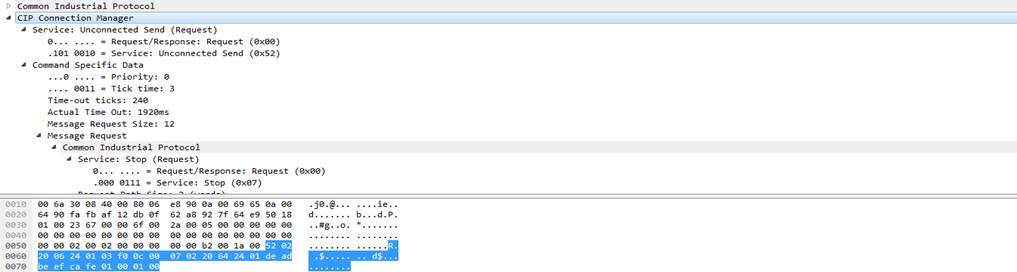
Improper Authentication Firmware Upload Vulnerability
Users are not properly authenticated, therefore there is a possibility that a user could upload new legitimate or malicious firmware image to the Ethernet card. The result can be a loss of availability, integrity and confidentiality while disrupting data transfer with other connected device.
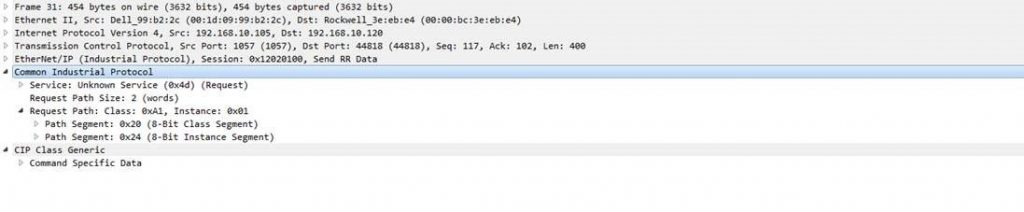
Mitigation
Rockwell recommends that all users update to the latest firmware and has since released patches to mitigate the vulnerabilities. Additionally, we recommend using a firewall with ingress/egress filtering and an intrusion detection system (IDS), validating all configurations. Using an IDS that performs deep packet inspection helps users visualize their entire network and allows for creation of security policies that alert operators to combinations of service codes, classes and attributes in CIP that can cause operational malfunctions to industrial devices as well as security issues.
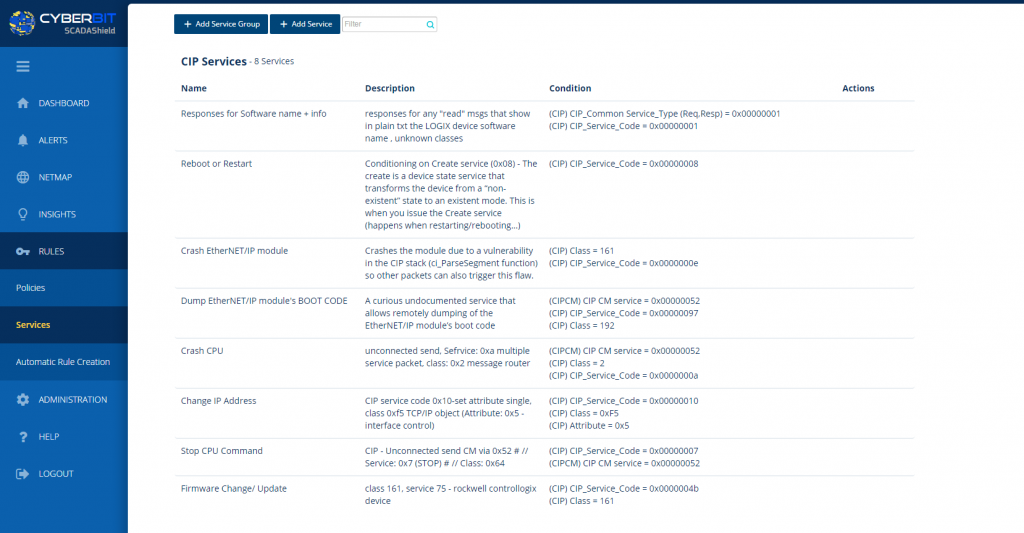
Using a DPI-based IDS to define CIP service codes, such as CPU Stop Packet, that may result in malicious activity or service disruption.
Screen shot: Cyberbit SCADAShield
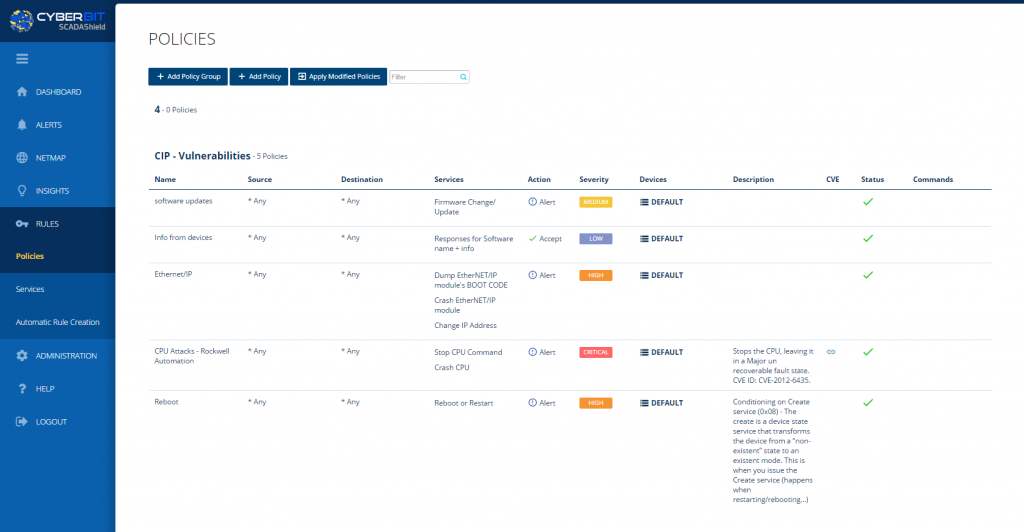
Using a DPI-based IDS to define security and operational policies, to address CIP vulnerabilities
Screen shot: Cyberbit SCADAShield
OT managers and analysts should also use open source signature-based network intrusion detection systems like Snort and Suricata can also help operators recognize patterns within packets that can cause operational malfunction as well as security issues.
Here is an example of a Snort rule alerting operators to potentially malicious activity;
Rockwell firmware upload attempt – The system will create an alert in the case of a TCP packet that contains the following bytes, \x20\xa1|\x21\x00\xa1\x00, was sent from an external and unauthorized network ($EXTERNAL_NET) to Rockwell PLC in the industrial network ($HOME_NET).
- alert tcp $EXTERNAL_NET any -> $HOME_NET 44818 (msg:”PROTOCOL-SCADA Rockwell firmware upload attempt”; flow:to_server,established; content:”|6F 00|”; content:”|00 00 00 00|”; within:4; distance:6; content:”|00 00 00 00|”; within:4; distance:8; pcre:”/(\x20\xa1|\x21\x00\xa1\x00)(\x24[\x01-\xff]|\x25\x00[\x01-\xff]\x00)/smi”; reference:cve,2012-6437; reference:url,tools.cisco.com/security/center/viewAlert.x?alertId=27868; classtype:policy-violation; sid:40333; rev:1;)
Rockwell Controllogix Stop CPU attempt – The system will create an alert in case a TCP packet that contains the following bytes: 07 02 20 64 24 01, was sent from an external and unauthorized network ($EXTERNAL_NET) to Rockwell PLC in the industrial network ($HOME_NET).
- alert tcp $EXTERNAL_NET any -> $HOME_NET [2222,44818] (msg:”PROTOCOL-SCADA Rockwell Controllogix Stop CPU attempt”; flow:to_server,established; content:”|6F 00|”; depth:2; content:”|00 00 00 00|”; within:4; distance:22; byte_extract:2,10,cipsize,relative; content:”|07 02 20 64 24 01|”; within:cipsize; classtype:policy-violation; sid:40518; rev:2;)
Final Note: The Urgency of Securing ICS/SCADA Networks
None of the above attacks require all that much skill to pull off, in fact, according to The Department of Homeland Security, an attacker only needs intermediate-level abilities to carry out an exploit that could send a plant offline. Consequently, operational network managers must be aware of the many ICS/SCADA protocol vulnerabilities. As attackers become more aware of the potential impact, it becomes all the more important to manage these vulnerabilities before they are exploited. And the longer vulnerabilities are left to fester, the greater the damage can be.
This is why it’s essential to understand the entire scope of your OT network and expose risks in real-time. The key lies in learning how your system behaves, identifying risks to security and continuity within moments of occurrence, for example by using a DPI-based IDS for industrial control networks, and addressing those areas before they have the opportunity to disrupt operations. To understand CIP vulnerabilities, as well as other vendor vulnerabilities, visit the ICS CERT site, identify whether your vendor version is vulnerable and download the latest patch. Get up to speed with industry standards such as NIST, and implement their recommendations.
It’s time for businesses to step up to the challenge of securing their ICS/SCADA networks, ensuring that our critical vectors remain safe from attack.
Download ENCS Report Executive Summary
Liran Eldar is ICS/SCADA security systems engineer at Cyberbit

