The days when ICS networks were isolated, air-gapped networks running specialized proprietary hardware and software are long gone. Critical infrastructure ICS networks have evolved rapidly in the past few years and now use numerous IP devices that connect to the internet to allow connectivity, remote access management and significant improvements in operational efficiency. But all of this technological advancement comes with a serious price; ICS networks are now at high risk for cyberattacks that can both disrupt operations and cause physical damage. ICS network managers are in the midst of leading massive cybersecurity overhauls to get up to date and the new gold standard guiding the industry is the NIST Critical Infrastructure Cybersecurity guideline.
NIST Cybersecurity Framework
The NIST Framework for Improving Critical Infrastructure Cybersecurity is a comprehensive industry standard for the cybersecurity of ICS networks. The guideline addresses every aspect of cybersecurity protection for the operational networks that are the backbone of critical services such as energy, water and sewage, transportation as well as chemical and pharmaceutical industries, pulp and paper, food and beverage and discrete manufacturing.
IT and OT Security – Same, but Different
Securing OT networks against cyber threats is in some ways very similar to what IT departments have been doing for decades, but OT networks also have some very unique characteristics and requirements that necessitate a new, specialized approach and unique solutions. The main difference is that ICS networks control physical machinery in the real world. So cyberthreats can potentially become physical threats. In the IT world hackers can steal data, hold computer systems for ransom and take websites or services offline. In the world of critical infrastructure, hackers can potentially cause machines to malfunction, even leading to real physical damage, such as was seen in the STUXNET attack where centrifuges at the Iranian nuclear plant were given faulty commands to spin at high speeds then suddenly halt, causing damage to the aluminum centrifuges that effectively took them offline for months.
STUXNET proved that cyber-attacks could lead to physical damage and ICS managers now have to defend their networks against similar attacks that could potentially cause costly production losses and even negatively impact a nation’s economy. One’s imagination can run wild with ideas of how malicious actors could take advantage of the cyber-vulnerability of ICS networks. Industrial warfare could include taking a major automotive manufacturer’s factory offline, altering machine-controlled processes of chemical or water treatment plants to disrupt supply or causing physical damage to discrete manufacturing equipment. Nation-state actors could cause disruption and panic by hacking transportation control systems for street lights or public transportation. But we don’t need to conjure up dramatic Hollywood-style doomsday scenarios, simply disrupting production or supply of critical infrastructure service is an unacceptable risk.
NIST Cybersecurity Framework Critical Infrastructure Core Functions
The NIST Framework lays out five core high-level cybersecurity functions that should be used to organize risk management, decision making, threat response and continuously learning and adapting for ongoing improvement and strengthening of an organizations’ cybersecurity. The core framework functions are: Identify, Protect, Detect, Respond and Recover.
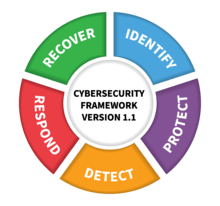
According to NIST, “These Functions are not intended to form a serial path or lead to a static desired end state. Rather, the Functions should be performed concurrently and continuously to form an operational culture that addresses the dynamic cybersecurity risk.”
4 Tiers of NIST Cybersecurity Framework for Critical Infrastructure
The new NIST framework takes into consideration the fact that cybersecurity is a relatively new area of expertise for most critical infrastructure ICS management teams, and thus describes a continuum of preparedness.
Tier 1: Partial
Tier 2: Risk-Informed
Tier 3: Repeatable
Tier 4: Adaptive
According to NIST, “Tiers are meant to support organizational decision making about how to manage cybersecurity risk, as well as which dimensions of the organization are a higher priority and could receive additional resources. Progression to higher Tiers is encouraged when a cost-benefit analysis indicates a feasible and cost-effective reduction of cybersecurity risk.” Obviously, ICS managers and the cybersecurity industry should be focused on ‘feasible and cost-effective’ ways to improve security so that every organization can quickly move towards Tier 4 implementation of adaptive cybersecurity.
Achieving Tier 4 NIST Cybersecurity Framework Implementation
ICS managers can begin by realistically assessing their current cybersecurity maturity tier, then develop an actionable plan to bring their organization up to tier 4; from basic perimeter security to continuous ICS threat monitoring, asset discovery and threat intelligence. This also includes behavioral analytics and machine learning technologies that can detect anomalous behavior quickly.
Tier 4 adaptive cybersecurity includes:
Risk Management Process – The organization adapts its cybersecurity practices based on previous and current cybersecurity activities, including lessons learned and predictive indicators. Through a process of continuous improvement incorporating advanced cybersecurity technologies and practices, the organization actively adapts to a changing threat and technology landscape and responds in a timely and effective manner to evolving, sophisticated threats.
Integrated Risk Management Program – There is an organization-wide approach to managing cybersecurity risk that uses risk-informed policies, processes, and procedures to address potential cybersecurity events. The relationship between cybersecurity risk and organizational objectives is clearly understood and considered when making decisions. Senior executives monitor cybersecurity risk in the same context as financial risk and other organizational risks. The organizational budget is based on an understanding of the current and predicted risk environment and risk tolerance. Business units implement the executive vision and analyze system-level risks in the context of the organizational risk tolerances. Cybersecurity risk management is part of the organizational culture and evolves from an awareness of previous activities and continuous awareness of activities on their systems and networks. The organization can quickly and efficiently account for changes to business/mission objectives in how risk is approached and communicated.
External Participation – The organization understands its role, dependencies, and dependents in the larger ecosystem and contributes to the community’s broader understanding of risks. It receives, generates, and reviews prioritized information that informs the continuous analysis of its risks as the threat and technology landscapes evolve. The organization shares that information internally and externally with other collaborators. The organization uses real-time or near real-time information to understand and consistently act upon cyber supply chain risks associated with the products and services it provides and that it uses. Additionally, it communicates proactively, using formal (e.g. agreements) and informal mechanisms to develop and maintain strong supply chain relationships.
Source: Framework for Improving Critical Infrastructure Cybersecurity version 1.1, 16 April 2018, NIST
How to Achieve Tier 4 NICS Compliance?
Once you have thoroughly reviewed the NIST Framework and assessed the current state of cybersecurity on your ICS network, it’s time to start making a practical plan to improve security. Even organizations currently at Tier 1 or 2 can achieve Tier 4 with careful planning, training and selection of cybersecurity tools.

