The SOC – a New Vision with New Challenges
The concept of a security operations center (SOC) is increasing in popularity. Many large enterprises have established SOCs, and others are in the planning process. SOCs maximize enterprise security impact by consolidating and centralizing cyber security incident prevention, detection and response across the entire organization. They also typically handle security monitoring, vulnerability management and many additional functions.
Large enterprise SOCs may monitor hundreds of thousands of endpoints and servers across multiple networks, and manage thousands of events every week. They centralize input from numerous sensors and data sources, which include threat intelligence, EDR, IPS, IDS and more. These disparate products and feeds are represented in numerous dashboards, applications and even different databases. The SIEM, today’s SOC management platform, does not address this challenge. As a result, 29 percent of organizations report the average remediation time is two to seven days, as concluded by a recent SANS survey.
Sound complex? It is. Furthermore, today’s attacks are highly tailored and extremely difficult to detect. They may dwell in the organizational network for months, performing reconnaissance and planning the optimal penetration tactic. On the flipside, emerging attack methods, such as ransomware, can be highly time-sensitive and require response within seconds.
Addressing operational complexity
So how can your SOC analyst be effective in this demanding, dynamic and critical environment?
Complex operational environments such as defense systems, air traffic control and energy infrastructure all require precision, 24/7 monitoring and zero tolerance for errors. To address these needs, they use advanced command and control systems to support the operational procedures and workflows, increase visibility and significantly reduce the chance of errors.
Security operations are no different. Today, SOC automation and orchestration tools transform the SOC into the command and control center it needs to be. These tools address the challenge in several ways:
Visibility – A single pane of glass integrates disparate feeds to present the analyst with a complete picture of the cyber campaign delivered as a unified dashboard.
Event triage – SOC orchestration prioritizes incidents and events to make sure critical and time-sensitive incidents will not disappear beneath a pile of noise.
Event correlation – Connect the dots between multiple “blips” to highlight events relating to the same targeted attack, as well as show analysts whether a similar event has happened in the past, so they can leverage organizational knowledge to manage it more effectively.
Workflow automation – Assist the SOC team in executing the organizational response procedures and manage response tools when applicable.
SOC automation platforms streamline the management of security events that may occur by the thousands in your enterprise, including unauthorized USB device usage, unlocking and replacing passwords, disseminating alerts, and providing internal and external reports. By automating labor-intensive tasks, the platforms can save more than 50 percent of the operational workload and dramatically improve your SOC’s impact.
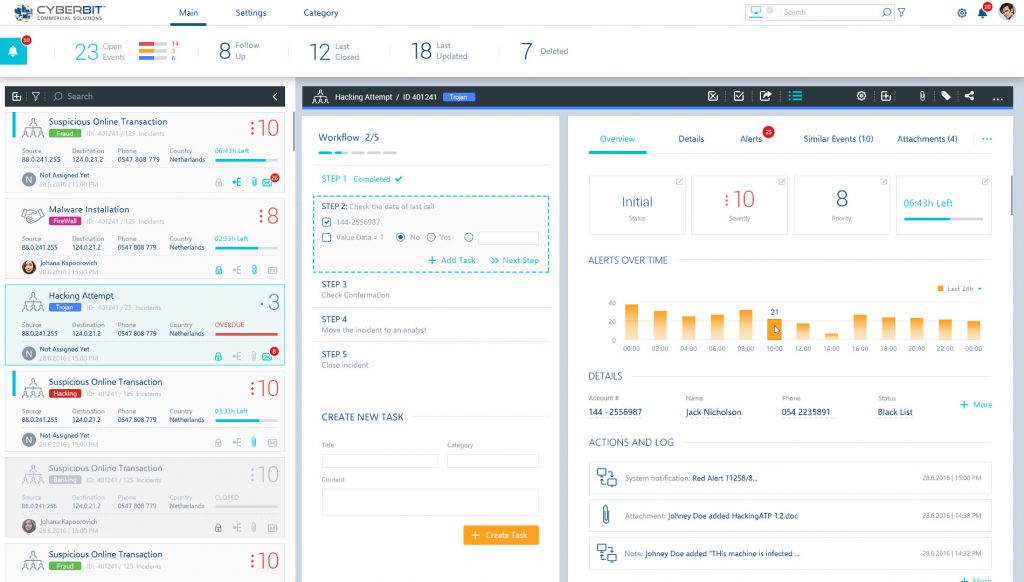
Cyberbit SOC 3D SOC Automation Platform – Screen Shot
The future of SOC
As security breaches become a primary business risk, the importance of SOC automation and orchestration increases. Managing a cyber crisis involves multiple stakeholders beyond the SOC, including business entities, legal, PR, C-level executives and more. They should be informed and occasionally take action during a breach. Compliance regulations require adhering to predefined workflows, which are executed in the SOC. Overall, the SOC is becoming the quarterback of the cyber breach process and is required to manage complicated, often high-profile events across the organization. Therefore, SOC automation and orchestration tools will be an essential building block in any new-generation SOC in order for companies to keep up with these needs.
I encourage you to learn more by viewing our teams’ next-generation SOC webinar.
Adi
Adi Dar is the CEO of Cyberbit

