It is in the best interest of any SOC manager or Information Security professional to invest in effective red team exercises to gain a comprehensive understanding of the vulnerabilities of their network.
If you are a SOC manager or a CISO employing a red team or a penetration-testing team you already know that keeping them skilled is essential. At the end of the day, these are the people in charge of auditing your infrastructure and finding the loopholes that all other systems could not locate.
Red team exercises not only detect network vulnerability, they also provide you with fresh insights regarding the impact a breach will have on your organization including which areas that breach would hit hardest, detect unpatched or weak spots in your security, development and testing protocols as well as test your ability to respond to a wide variety of incidents.
Unlike blue team exercises, red team exercises have clear goals in mind and do not typically adhere to a specific time limit. These exercises follow a testing method to find the weaknesses of your network and, in order to train employees to be aware and prepared, explain how they were able to gain access, justifying any costly investment that might have previously raised doubts.
How Red Team Exercises Work
Successful red team exercises will provide you with a clear picture of where and how a hacker can breach your network, and how much damage that will cause to your business. In most cases, an outsourced red team expert is hired, well equipped with the ability and expertise in security vulnerabilities, however, no knowledge of your infrastructure’s defense networks.
Red team exercises use various techniques including phishing and social engineering aimed directly at your employees or their usernames and passwords, in addition to watering hole attacks and drive-by downloads that target specific users and their PC using an internet browser or installing malware on a site visited by the specific user.
There are a few exercises your red team can implement immediately in order to fully optimize your organization’s ability to protect itself and reduce any false sense of security you might have.
CI Flaw Red Team Exercise
Red Team Objective: to gain the highest form of access to all domains of your network.
In this pen testing exercise, red team experts use all available methods as well as Kali Linux, a tool designed for digital forensics that contains all the most crucial preinstalled penetration testing programs, providing your red team with all they need to successfully execute this exercise. In this exercise, red team experts have no access to the network diagram and must begin to map it out from scratch using expert pen testing techniques. Their endgame objective is to access domain admin privileges which will then allow them to attack your entire network with very little restrictions.
By assuming the position of a hacker, using every tool at their disposal, you can gain valuable insights as to a hacker’s methodology for attaining access as well as the amount of damage they can cause, and which resources need to be invested to improve your security protocols.
Further, this exercise is an effective way to train your SOC team members to understand how to respond and prevent future attacks, which is a crucial asset.
CI Flaw exercises usually span between 3-6 hours, depending on the proficiency of the red team pen tester. Once completed, a SOC manager or CISO will first understand whether a breach was possible, and in most cases, it is. If a breach was possible, the following metrics presented should surround the amount of damage this breach, or others, can cause the organization.
Finally, the red team expert should submit a detailed report explaining all the methods used to successfully attack the network as well as descriptions of the reasons for the vulnerabilities detected, which could be a result of several reasons, from unpatched versions and older, non-updated programs to inconsistencies in an organization’s security policy.
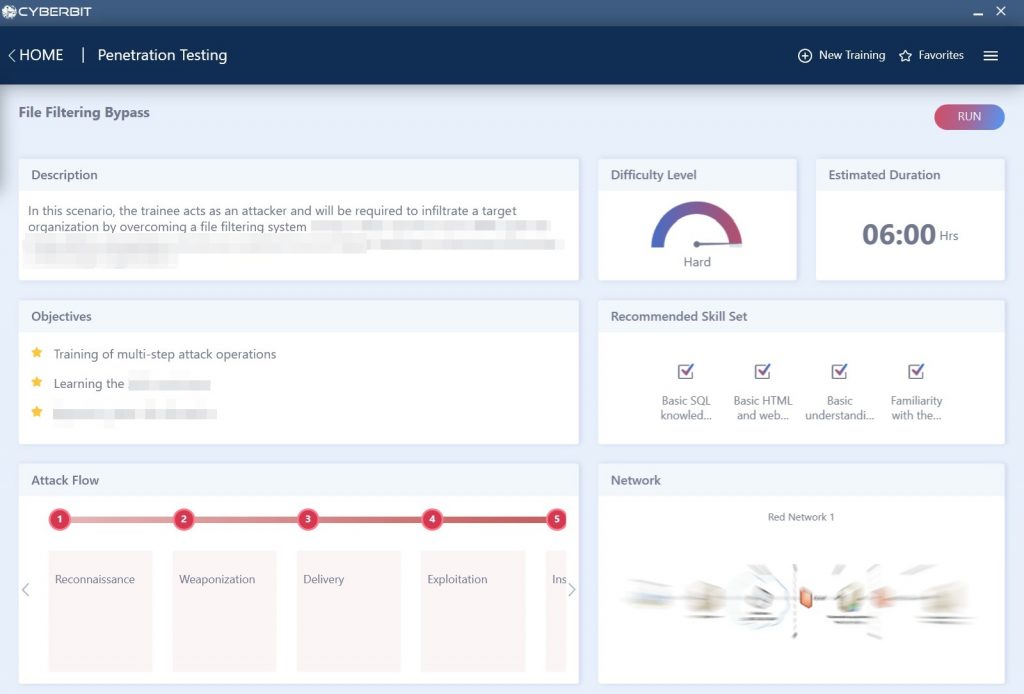
File Filtering Red Team Exercise on Cyberbit Range
File Filtering Bypass Scenario
Red Team Objective: to imitate and initiate an external attack on your network
This exercise tests your web-based vulnerability by overcoming a file filtering system using an SQL injection while testing the weaknesses of your network against external attacks. External attacks are made easier when the operating network or program is outdated or past its end-of-life period and has not implemented the proper security patches to ensure continued protection. Unfortunately, this is a common mistake that can cost massive amounts of money, resources and end users, as we witnessed in May of 2015 with the WannaCry ransomware attack, where over 200,000 people and 300,000 computers were infected due to lack of proper patches or updated programs.
This test will give you an understanding of which employees at your organization are vulnerable to such an attack due to insufficient updates or improper protection processes, which will help prevent an attack like this from spreading throughout your network.
In addition, the facilitation of such an exercise gives proper knowledge into changes you might need to make to fortify your network, such as a solution that forces employees to update their web browsers or programs, which is perfect for large corporations where not every employee is cybersecurity inclined.
These exercises take up to 6 hours, and like the CI Flaw exercise, is dependent on the skill and experience of the tester. This exercise should relay exactly how many vulnerable, unpatched programs or operating systems are present in a network, allowing SOC managers and CISOs to comprehend which computers need updating and which employees need basic cybersecurity awareness and training.
For the road…
Depending on its complexity, your red team exercise could run anywhere between two weeks to a couple of months but is a worthy investment when considering the resources and expenses it could save by preventing a breach. Once your red team has completed their tests and exercises, an in-depth debrief should occur in which they describe the conclusions they’ve arrived at, successes, failures and test methodologies as well as preventative measure training.
Your red team mimics the attacks a hacker could perform on your organization’s networks, exposing your most vulnerable areas. This is pertinent to understanding your strengths and weaknesses when facing such events, in addition to how to improve and prevent for the future.
Red teams differ greatly from blue and purple teams, which will be discussed in later blogs, however, combined, give you all the peace of mind you need to operate safely and maintain the security of your network, employees, end users and data.
Download FREE: Cyberbit Enterprise Cyber Awareness and Simulation Exercise Guide
Kobi Leizerovich is an experienced cybersecurity trainer and has delivered thousands of training sessions to enterprise SOC teams, red teams and military cyber experts.