It is no news that cyber attacks are increasing in volume, severity, and complexity with cyber resilience being more difficult to achieve. Sophisticated, multi-vector attacks can quickly overwhelm security teams causing substantial damage and breaches not only on IT networks but also on OT (SCADA) networks and today even on the growing infrastructure of IoT. Organizations must re-assess their networks’ cyber resilience in light of this changing landscape.
Digitization creates network vulnerabilities
The digitization of information and the more recent digitization of industrial infrastructure is no less than a revolution. Unsurprisingly, this drastic change creates an opportunity for cyber attackers resulting in challenges that organizations are far from adapting to. IT and OT networks were designed in layers and built patch over patch in an attempt to keep up with the dynamic nature of enterprise IT and with the evolvement of cyber threats. Throughout this evolutionary process, have we ever stopped to assess and optimize the resilience of our entire network security architecture? Did we ever adapt our IT and OT networks to the thousands of next generation multi-vector advanced persistent threats (APTs) that are out there in the wild? And no less importantly – do we have the tools to analyze our networks and test them against these kinds of evolving threats?
In most cases, the answer to these questions is No.
Clearly, it is time to catch up. But how do we practically test our resilience in a way that is effective, realistic as possible, but doesn’t pose a danger to mission critical networks and assets?
Simulations improve readiness
Militaries have been using virtual simulation technology to test their readiness for battle for decades. In simulated drills, they test and measure technologies, processes and people in the safety of virtual battlefields. Cybersecurity organizations should learn from their military counterparts and test their mission-critical systems, best practices, operational procedures and team readiness, in virtual testing grounds that are as true-to-life as possible.
Cyber range simulation
A Cyber range, often used as a training tool, is also one of the most effective testbeds for simulating and testing your network, hardware, software and cybersecurity tools. It can be used to examine your tools’ effectiveness against cyber attacks, including complex and evolving ones. We see more organizations adopting this approach of using a cyber range to evaluate their planned network architecture, evaluate new systems, test existing ones, and identify gaps in networks, tools, and processes. Organizations often feel they are covered if they use a suite of best-of-breed cyber security products. However, this false sense of security disappears once a new attack worms its way through vulnerabilities, causing the layered security mechanisms and network segregation to collapse and crumble. This is why it’s so important to test your environment in realistic, multi-stage, sometimes even non-recoverable attack scenarios before the real doomsday breach hits us and our network faces the harsh reality.
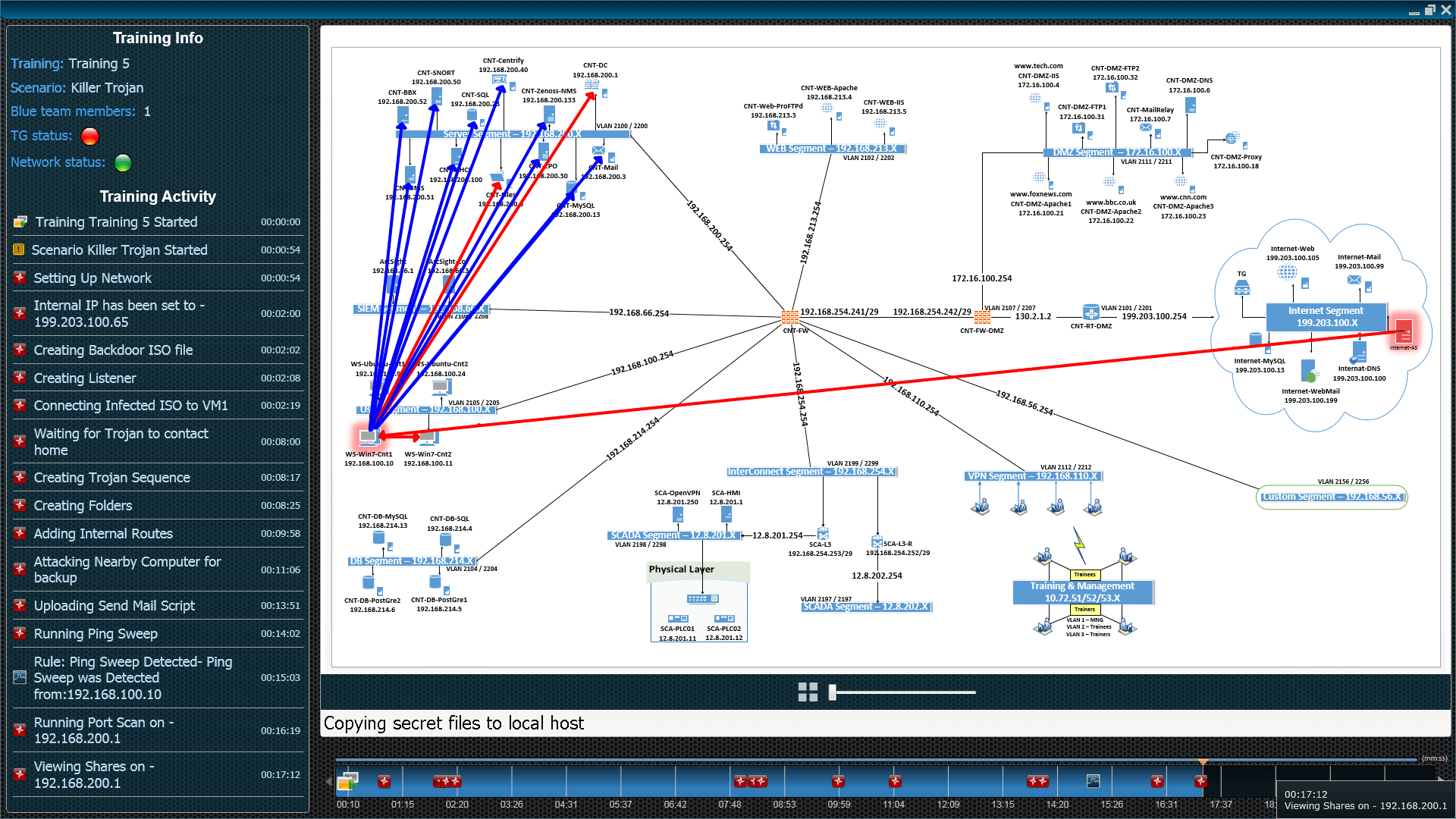
Training scenario timeline and attack diagram, Cyberbit Range
Using simulation to improve network resilience
Since we are facing these multi-stage, multi-vector attacks situations on highly complex and ever-changing networks and assets we can no longer rely on our gut feeling or anecdotal experience to determine if our systems are secure and operational-ready. As with any critical system, we need reliable, tested and proven methodologies, and the technologies to support and evaluate them based on clear engineering parameters.
Working with many customers in the MSSP, public sector and enterprise space, we’ve found that one of the best ways to achieve effective system and operational evaluation and achieve the desired cyber resilience, is by using simulation platforms. Without them, companies are not investing their security resources effectively. Instead, they choose to keep living a make-believe network security fantasy until the next big cyber attack jars them awake.
Adi Dar is CEO of Cyberbit

